
|
시장보고서
상품코드
1811733
제로 트러스트 네트워크 액세스(ZTNA) 시장 : 제공 제품별, 전개 모드별, 조직 규모별, 응용 분야별, 업계별, 지역별 예측(-2030년)Zero Trust Network Access (ZTNA) Market by Solution (Agent-based, Agentless, Universal) and Application Area (Remote Workforce Access, Third-party & BYOD Access, Private Application Access, Workload-to-Workload & API Access) - Global Forecast to 2030 |
||||||
전 세계 ZTNA(Zero Trust Network Access) 시장 규모는 2025년 13억 4,000만 달러에서 2030년에 41억 8,000만 달러로 성장했으며, 예측 기간 동안 연평균 성장률(CAGR)은 25.5%를 나타낼 전망입니다.
기업들이 원격 근무와 클라우드 기반 용도들을 도입함에 따라 핵심 자원에 대한 접근을 보호하는 것이 최우선 과제가 되었습니다. 기업들은 승인된 사용자만 민감한 데이터와 시스템에 접근할 수 있도록 보장하고자 합니다. 제로 트러스트 네트워크 액세스(ZTNA) 솔루션은 이러한 보안 문제를 해결하는 데 핵심적입니다.
| 조사 범위 | |
|---|---|
| 조사 대상 연도 | 2019-2030년 |
| 기준 연도 | 2024년 |
| 예측 기간 | 2025-2030년 |
| 검토 단위 | 금액(100만 달러/10억 달러) |
| 부문 | 제공 제품별, 전개 모드별, 조직 규모별, 응용 분야별, 업계별, 지역별 |
| 대상 지역 | 북미, 유럽, 아시아태평양, 중동, 아프리카, 라틴아메리카 |
ZTNA는 또한 무단 접근 및 잠재적 데이터 유출 위험을 감축하는 데 도움이 됩니다. 피싱, 랜섬웨어 또는 내부자 위협과 같은 사이버 공격은 조직에 상당한 재정적 손실과 평판 손상을 초래할 수 있습니다. 그러나 ZTNA 솔루션은 레거시 애플리케이션 및 기존 온프레미스 인프라와의 호환성이 제한적입니다. 특히 제조, 정부, 의료 분야를 비롯한 많은 기업은 최근 신원 중심 보안 프레임워크를 위해 설계되지 않은 구식 레거시 시스템에 여전히 의존하고 있습니다.

기업들이 제로 트러스트 아키텍처의 전개, 관리 및 최적화를 위한 전문가 지원을 점점 더 많이 요구함에 따라 서비스 부문은 ZTNA 시장에서 급속한 성장을 가지고 있습니다. IT 환경의 복잡성이 증가하고 안전한 원격 접근에 대한 필요성이 커짐에 따라 기업들은 원활한 구현과 연속 모니터링을 보장하기 위해 전문 서비스로 눈을 돌리고 있습니다. 이러한 서비스는 조직이 전문가의 지침, 신속한 사고 대응, 지속적인 최적화의 혜택을 누릴 수 있도록 하여 운영상의 어려움을 최소화하면서 강력한 보안 태세를 유지하는 데 도움을 줍니다.
조직들이 분산된 팀과 클라우드 기반 운영을 점점 더 뒷받침함에 따라 원격 근무자 접근 부문은 ZTNA 시장에서 상당한 성장을 경험하고 있습니다. 직원들이 다양한 위치와 기기에서 기업 자원에 접근함에 따라 기업들은 민감한 데이터를 보호하기 위해 안전하고 원활한 연결성을 최우선으로 합니다. ZTNA 솔루션은 세분화된 신원 기반 접근 제어를 제공하여 무단 접근 및 데이터 유출 위험을 감축합니다. 이러한 기능은 조직이 규정 준수 및 보안을 보장하면서 생산성을 유지할 수 있게 하여 원격 근무자 접근을 위한 ZTNA의 광범위한 채택을 촉진하고 있습니다.
북미는 디지털 고급 기업의 집중, 원격 및 하이브리드 근무의 광범위한 채택, 그리고 ZTNA를 보다 광범위한 보안 서비스 엣지(SSE) 및 보안 액세스 서비스 엣지(SASE) 프레임워크에 조기에 통합한 덕분에 ZTNA 미래를 계속해서 기록하고 있습니다. 미국과 캐나다에서는 다양한 산업의 조직들이 레거시 VPN의 한계, 규정 준수 요구사항, 진화하는 사이버 위협으로 인해 상당한 어려움을 겪고 있습니다. 이러한 요인들은 신원 및 컨텍스트 기반의 지속적이고 안전한 접근을 제공하는 제로 트러스트 네트워크 액세스(ZTNA) 솔루션으로의 전환을 촉진하고 있으며, 이는 독립형 ZTNA 제품과 클라우드 네이티브 플랫폼을 통해 제공되는 통합 ZTNA 기능의 강력한 채택으로 이어지고 있습니다.
한편 아시아태평양(APAC) 지역은 예측 기간 동안 가장 높은 연평균 복합 성장률(연평균 성장률(CAGR))을 기록할 것으로 전망됩니다. 인도, 중국, 일본 및 동남아시아 전역에서 가속화되는 클라우드 도입, 증가하는 사이버 사고, 정부 주도의 디지털 전환 이니셔티브가 성장을 주도하고 있습니다. 해당 지역의 많은 중소기업 및 중견 기업들은 VPN에 대한 비용 효율적인 대안으로 ZTNA를 채택하여 막대한 인프라 투자 없이도 안전한 원격 접속을 가능하게 하고 있습니다. 제로 트러스트 도입에 대한 정부 의무화 및 모바일 우선, 원격 근무 인력의 확대되기는 아시아태평양 전역에서 ZTNA 전개 속도를 더욱 가속화하고 있습니다.
본 보고서에서는 세계의 제로트러스트 네트워크 액세스(ZTNA) 시장에 대해 조사했으며, 제공 제품별, 전개 모드별, 조직 규모별, 응용 분야별, 업계별, 지역별 동향 및 시장 진출기업 프로파일 등을 정리했습니다.
목차
제1장 서론
제2장 조사 방법
제3장 주요 요약
제4장 중요 인사이트
제5장 시장 개요와 업계 동향
- 소개
- 시장 역학
- 사례 연구 분석
- 밸류체인 분석
- 생태계 분석
- 생성형 AI가 제로 트러스트 네트워크 액세스 시장에 미치는 영향
- Porter's Five Forces 분석
- 주요 이해관계자와 구매 기준
- 가격 분석
- 기술 분석
- 특허 분석
- 규제 상황
- 미국 관세의 영향 : 제로 트러스트 네트워크 액세스 시장(2025년)
- 고객사업에 영향을 주는 동향 및 혼란
- 제로 트러스트 네트워크 액세스 시장 : 비즈니스 모델
- 주요 컨퍼런스 및 이벤트(2025년)
- 투자 및 자금조달 시나리오
제6장 제로 트러스트 네트워크 액세스 시장(제공 제품별)
- 소개
- 솔루션
- 서비스
제7장 제로 트러스트 네트워크 액세스 시장(전개 모드별)
- 소개
- 클라우드
- 하이브리드
제8장 제로 트러스트 네트워크 액세스 시장(조직 규모별)
- 소개
- 대기업
- 중소기업
제9장 제로 트러스트 네트워크 액세스 시장(응용 분야별)
- 소개
- 원격 근무자 액세스
- 타사/계약자 및 BYOD 액세스
- 특권/관리자 액세스
- SAAS 용도 액세스 제어
- 비공개 용도 액세스
- 워크로드 간 및 API 액세스
제10장 제로 트러스트 네트워크 액세스 시장(업계별)
- 소개
- BFSI
- 정부 및 공공 부문
- 소매 및 전자상거래
- 정보기술(IT)과 정보기술 대응 서비스(ITES)
- 헬스케어
- 교육
- 제조
- 기타
제11장 제로 트러스트 네트워크 액세스(ZTNA) 시장(지역별)
- 소개
- 북미
- 북미 : 제로 트러스트 네트워크 액세스 시장 성장 촉진요인
- 북미 : 거시경제 전망
- 미국
- 캐나다
- 유럽
- 유럽 : 제로 트러스트 네트워크 액세스(ZTNA) 시장 성장 촉진요인
- 유럽 : 거시경제 전망
- 영국
- 독일
- 프랑스
- 이탈리아
- 기타
- 아시아태평양
- 아시아태평양 : 제로 트러스트 네트워크 액세스(ZTNA) 시장 성장 촉진요인
- 아시아태평양 : 거시경제 전망
- 중국
- 일본
- 인도
- 기타
- 중동 및 아프리카
- 중동 및 아프리카 : 제로 트러스트 네트워크(ZTNA) 시장 성장 촉진요인
- 중동 및 아프리카 : 거시경제 전망
- GCC 국가
- 남아프리카
- 기타
- 라틴아메리카
- 라틴아메리카 : 제로 트러스트 네트워크 액세스(ZTNA) 시장 성장 촉진요인
- 라틴아메리카 : 거시경제 전망
- 브라질
- 멕시코
- 기타
제12장 경쟁 구도
- 주요 참가 기업의 전략 및 강점(2020-2024년)
- 수익 분석(2020-2024년)
- 시장 점유율 분석(2024년)
- 브랜드, 제품 비교
- 기업평가와 재무지표
- 기업평가 매트릭스 : 주요 진입기업(2024년)
- 기업평가 매트릭스 : 스타트업, 중소기업(2024년)
- 경쟁 시나리오
제13장 기업 프로파일
- 소개
- PALO ALTO NETWORKS
- ZSCALER
- CLOUDFLARE
- CHECK POINT
- FORTINET
- MICROSOFT
- CISCO
- FORCEPOINT
- TELEPORT
- IVANTI
- NETSKOPE
- IBOSS
- APPGATE
- FORTRA
- BROADCOM
- CITRIX
- SOPHOS
- AKAMAI
- SONICWALL
- MENLO SECURITY
- CLOUDBRINK
- VERSA NETWORKS
- NETFOUNDRY
- JAMF
- DEFENSX
- ALKIRA
- XAGE SECURITY
- HILLSTONE NETWORKS
- SYSTANCIA
- ACCOPS
제14장 인접 시장
제15장 부록
HBR 25.09.22The global zero trust network access (ZTNA) market size is projected to grow from 1.34 billion in 2025 to USD 4.18 billion by 2030 at a CAGR of 25.5% during the forecast period. As organizations adopt remote work and cloud-based applications, securing access to critical resources has become a top priority. They want to ensure only authorized users can access sensitive data and systems. Zero trust network access (ZTNA) solutions are crucial in addressing these security concerns.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/USD Billion) |
| Segments | Offering, Deployment mode, Organization size, Application area, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
ZTNA also helps to reduce the risk of unauthorized access and potential data breaches. Cyberattacks, such as phishing, ransomware, or insider threats, can lead to significant financial and reputational damage for organizations. However, the limited compatibility of ZTNA solutions with legacy applications and traditional on-premises infrastructure. Many organizations, especially in manufacturing, government, and healthcare, still rely on outdated legacy systems that were not designed for modern, identity-centric security frameworks.
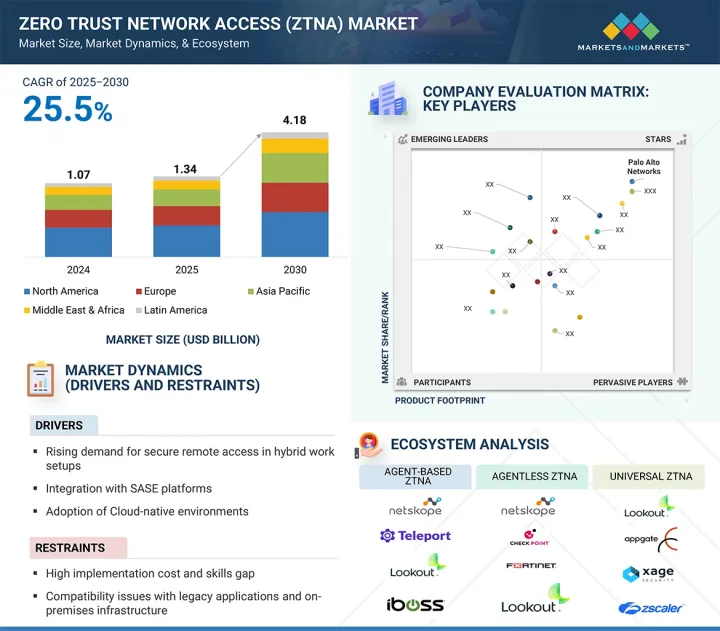
"By offering, the services segment will account for the highest CAGR during the forecast period"
The services segment is witnessing rapid growth in the ZTNA market as organizations increasingly seek expert support for deploying, managing, and optimizing Zero Trust architectures. With the rising complexity of IT environments and the growing need for secure remote access, enterprises are turning to professional services to ensure seamless implementation and continuous monitoring. These services enable organizations to benefit from expert guidance, faster incident response, and ongoing optimization, helping maintain a robust security posture while minimizing operational challenges.
"By application area, the remote workforce access segment will hold the largest market share during the forecast period"
The remote workforce access segment is experiencing significant growth in the ZTNA market as organizations increasingly support distributed teams and cloud-based operations. With employees accessing corporate resources from diverse locations and devices, businesses prioritize secure, seamless connectivity to protect sensitive data. ZTNA solutions provide granular, identity-based access control, reducing the risk of unauthorized access and data breaches. This capability enables organizations to maintain productivity while ensuring compliance and security, driving the widespread adoption of ZTNA for remote workforce access.
"North America is expected to hold the largest market share, while Asia Pacific is expected to witness the fastest growth during the forecast period"
North America continues to dominate the ZTNA landscape due to its concentration of digitally advanced enterprises, widespread remote and hybrid work adoption, and early integration of ZTNA into broader Secure Service Edge (SSE) and Secure Access Service Edge (SASE) frameworks. In the US and Canada, Organizations in various industries are encountering significant challenges due to legacy VPN limitations, compliance demands, and evolving cyber threats. These factors are driving a transition toward Zero Trust Network Access (ZTNA) solutions that offer continuous, secure access based on identity and context, thus leading to a strong uptake of standalone ZTNA offerings and integrated ZTNA capabilities delivered through cloud-native platforms.
Meanwhile, the Asia Pacific (APAC) region is projected to grow at the highest CAGR during the forecast period. Growth is fueled by rapid cloud adoption, rising cyber incidents, and government-backed digital transformation initiatives across India, China, Japan, and Southeast Asia. Many SMEs and mid-sized enterprises in the region are adopting ZTNA as a cost-effective alternative to VPNs, enabling secure remote access without heavy infrastructure investments. Government mandates on zero trust adoption and an expanding base of mobile-first and remote workforces are further accelerating ZTNA deployment across Asia Pacific.
Breakdown of Primaries
The study contains insights from various industry experts, from component suppliers to Tier 1 companies and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 35%, Tier 2 - 45%, and Tier 3 - 20%
- By Designation: C-level - 40%, Managerial & Other Levels - 60%
- By Region: North America - 50%, Europe - 20%, Asia Pacific - 20%, Rest of the World - 10%
The key players in the ZTNA market include Palo Alto Networks (US), Zscaler (US), Cloudflare (US), Microsoft (US), Check Point (Israel), Teleport (US), Cisco (US), Fortinet (US), Ivanti (US), Forcepoint (US), Netskope (US), iboss (US), Appgate (US), Lookout (US), Broadcom (US), Citrix (US), Sophos (UK), Akamai (US), Menlo Security (US), SonicWall (US), Cloudbrink (US), Versa Networks (US), NetFoundry (US), Jamf (US), DefensX (US), Alkira (US), Xage Security (US), Hillstone Networks (US), Systancia (France), and Accops (India). The study includes an in-depth competitive analysis of the key players in the ZTNA market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the ZTNA market and forecasts its size by Solutions (agent-based ZTNA, agentless ZTNA, universal ZTNA), Services (professional services, managed services), Deployment Mode (cloud-delivered, hybrid), by Organization Size (large enterprises, small and medium enterprises (SMEs)), Application Area (remote workforce access, third-party/contractor & BYOD access, privileged/administrative access, SAAS application access control, private application access, workload-to-workload & API/microservices access), Vertical (banking, financial services, and insurance (BFSI), government & public sector, retail & ecommerce, IT & ITeS, healthcare, education, manufacturing, other verticals (telecommunications, energy & utilities, travel & hospitality, and media & entertainment), and Region (North America, Europe, Asia Pacific, Middle East & Africa, and Latin America).
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders and new entrants with information on the closest approximations of the revenue numbers for the overall ZTNA market and the subsegments. It will also help stakeholders understand the competitive landscape and gain more insights to position their businesses better and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
- Analysis of key drivers (Growing need for secure remote access in hybrid and remote work environments, Integration into broader Secure Access Service Edge (SASE) platforms, Growing adoption of cloud-native environments, Increasing sophistication of targeted attacks on internal applications), restraints (High initial cost and skills gap in implementing ZTNA solutions, Compatibility issues with legacy applications and on-premises infrastructure, Complexity of policy configuration and identity management at scale), opportunities (Convergence of ZTNA with AI/ML for adaptive trust evaluation, Growth in industry-specific ZTNA solutions, Increasing investment from enterprises to replace aging VPN infrastructure) and challenges (User experience friction during continuous authentication, Visibility gaps across multi-cloud environments, Insider risk and policy complexity undermining ZTNA effectiveness, Platform lock-in and integration challenges in ZTNA deployments).
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the ZTNA market.
- Market Development: Comprehensive information about lucrative markets: the report analyses the MSS market across varied regions.
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the ZTNA market.
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players such as Palo Alto Networks (US), Zscaler (US), Cloudflare (US), Microsoft (US), Check Point (Israel), Teleport (US), Cisco (US), Fortinet (US), Ivanti (US), Forcepoint (US), Netskope (US), iboss (US), Appgate (US), Lookout (US), Broadcom (US), Citrix (US), Sophos (UK), Akamai (US), Menlo Security (US), SonicWall (US), Cloudbrink (US), Versa Networks (US), NetFoundry (US), Jamf (US), DefensX (US), Alkira (US), Xage Security (US), Hillstone Networks (US), Systancia (France), and Accops (India) in the ZTNA market.
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION AND REGIONAL SCOPE
- 1.3.2 INCLUSIONS AND EXCLUSIONS
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Breakup of primary interviews
- 2.1.2.2 Key insights from industry experts
- 2.2 MARKET SIZE ESTIMATION
- 2.2.1 TOP-DOWN APPROACH
- 2.2.2 BOTTOM-UP APPROACH
- 2.3 DATA TRIANGULATION
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN ZERO TRUST NETWORK ACCESS MARKET
- 4.2 ZERO TRUST NETWORK ACCESS MARKET, BY OFFERING
- 4.3 ZERO TRUST NETWORK ACCESS MARKET, BY SOLUTION
- 4.4 ZERO TRUST NETWORK ACCESS MARKET, BY SERVICE
- 4.5 ZERO TRUST NETWORK ACCESS MARKET, BY PROFESSIONAL SERVICE
- 4.6 ZERO TRUST NETWORK ACCESS MARKET, BY DEPLOYMENT MODE
- 4.7 ZERO TRUST NETWORK ACCESS MARKET, BY ORGANIZATION SIZE
- 4.8 ZERO TRUST NETWORK ACCESS MARKET, BY APPLICATION AREA
- 4.9 ZERO TRUST NETWORK ACCESS MARKET, BY VERTICAL
- 4.10 ZERO TRUST NETWORK ACCESS MARKET, BY REGION
- 4.11 MARKET INVESTMENT SCENARIO
5 MARKET OVERVIEW AND INDUSTRY TRENDS
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Growing need for secure remote access in hybrid and remote work environments
- 5.2.1.2 Increasing integration into broader SASE platforms
- 5.2.1.3 Rising adoption of cloud-native environments
- 5.2.1.4 Increasing sophistication of targeted attacks on internal applications
- 5.2.2 RESTRAINTS
- 5.2.2.1 High initial cost implementation and skills gap
- 5.2.2.2 Compatibility issues with legacy applications and on-premises infrastructure
- 5.2.2.3 Complexity of policy configuration and identity management at scale
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Convergence of ZTNA with AI/ML for adaptive trust evaluation
- 5.2.3.2 Growth in industry-specific ZTNA solutions
- 5.2.3.3 Increasing investment in aging VPN infrastructure replacements
- 5.2.4 CHALLENGES
- 5.2.4.1 Requirement for constant authentication
- 5.2.4.2 Visibility gaps across multi-cloud environments
- 5.2.4.3 Insider risk and policy complexity
- 5.2.4.4 Platform lock-in and integration challenges
- 5.2.1 DRIVERS
- 5.3 CASE STUDY ANALYSIS
- 5.3.1 NOV SECURES GLOBAL OPERATIONS WITH ZSCALER ZERO TRUST ARCHITECTURE, SAVING MILLIONS AND ENHANCING SECURITY
- 5.3.2 WEALDEN DISTRICT COUNCIL SECURES HYBRID WORKFORCE WITH PALO ALTO NETWORKS' ZTNA 2.0 AND AI-POWERED SASE
- 5.3.3 CANVA SECURES REMOTE COLLABORATION AND EDGE PERFORMANCE WITH CLOUDFLARE ZTNA AND SERVERLESS EDGE
- 5.3.4 BARNES GROUP IMPLEMENTS FORTINET UNIVERSAL ZTNA TO STRENGTHEN GLOBAL SECURITY, STREAMLINE OPERATIONS, AND CUT INTEGRATION TIME
- 5.3.5 VICTORIA UNIVERSITY BUILDS A ZTNA-ENABLED SMART CAMPUS WITH CISCO'S SD-ACCESS ARCHITECTURE
- 5.4 VALUE CHAIN ANALYSIS
- 5.4.1 RESEARCH AND DEVELOPMENT
- 5.4.2 SOLUTION PROVIDERS
- 5.4.3 INTEGRATION AND DEPLOYMENT
- 5.4.4 COMPLIANCE AND AUDITING
- 5.4.5 END USERS
- 5.5 ECOSYSTEM ANALYSIS
- 5.6 IMPACT OF GENERATIVE AI ON ZERO TRUST NETWORK ACCESS MARKET
- 5.6.1 GENERATIVE AI
- 5.6.2 TOP USE CASES AND MARKET POTENTIAL IN ZERO TRUST NETWORK ACCESS MARKET
- 5.6.3 IMPACT OF GENERATIVE AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- 5.6.3.1 Identity & access management (IAM) systems
- 5.6.3.2 Security service edge (SSE) & SASE platforms
- 5.6.3.3 Cloud access security brokers (CASB)
- 5.6.3.4 Endpoint security platforms (EDR/XDR)
- 5.6.3.5 IoT & OT security ecosystems
- 5.7 PORTER'S FIVE FORCES ANALYSIS
- 5.7.1 THREAT OF NEW ENTRANTS
- 5.7.2 BARGAINING POWER OF SUPPLIERS
- 5.7.3 BARGAINING POWER OF BUYERS
- 5.7.4 THREAT OF SUBSTITUTES
- 5.7.5 INTENSITY OF COMPETITION RIVALRY
- 5.8 KEY STAKEHOLDERS AND BUYING CRITERIA
- 5.8.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 5.8.2 BUYING CRITERIA
- 5.9 PRICING ANALYSIS
- 5.9.1 AVERAGE SELLING PRICE OF SOLUTIONS, BY KEY PLAYER
- 5.9.2 INDICATIVE PRICING ANALYSIS, BY KEY PLAYER, 2024
- 5.10 TECHNOLOGY ANALYSIS
- 5.10.1 KEY TECHNOLOGIES
- 5.10.1.1 Identity and access management (IAM)
- 5.10.1.2 Software-defined perimeter (SDP)
- 5.10.1.3 Cloud access security broker (CASB)
- 5.10.2 COMPLEMENTARY TECHNOLOGIES
- 5.10.2.1 Endpoint detection and response (EDR)
- 5.10.2.2 User and entity behavior analytics (UEBA)
- 5.10.2.3 Multi-factor authentication (MFA)
- 5.10.3 ADJACENT TECHNOLOGIES
- 5.10.3.1 Cloud computing
- 5.10.3.2 Blockchain
- 5.10.3.3 Internet of Things (IoT)
- 5.10.1 KEY TECHNOLOGIES
- 5.11 PATENT ANALYSIS
- 5.12 REGULATORY LANDSCAPE
- 5.12.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 5.12.2 KEY REGULATIONS
- 5.12.2.1 Payment Card Industry Data Security Standard (PCI-DSS)
- 5.12.2.2 General Data Protection Regulation (GDPR)
- 5.12.2.3 California Consumer Privacy Act (CCPA)
- 5.12.2.4 Gramm-Leach-Bliley Act of 1999 (GLBA)
- 5.12.2.5 Personal Information Protection and Electronic Documents Act (PIPEDA)
- 5.12.2.6 Health Insurance Portability and Accountability Act (HIPAA)
- 5.12.2.7 Federal Information Security Management Act (FISMA)
- 5.12.2.8 Sarbanes-Oxley Act (SOX)
- 5.12.2.9 International Organization for Standardization (ISO) - Standard 27001
- 5.13 IMPACT OF 2025 US TARIFF - ZERO TRUST NETWORK ACCESS MARKET
- 5.13.1 INTRODUCTION
- 5.13.2 KEY TARIFF RATES
- 5.13.3 PRICE IMPACT ANALYSIS
- 5.13.4 IMPACT ON COUNTRY/REGION
- 5.13.4.1 North America
- 5.13.4.2 Europe
- 5.13.4.3 Asia Pacific
- 5.13.5 IMPACT ON END-USE INDUSTRIES
- 5.14 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.15 ZERO TRUST NETWORK ACCESS MARKET: BUSINESS MODELS
- 5.16 KEY CONFERENCES AND EVENTS, 2025
- 5.17 INVESTMENT AND FUNDING SCENARIO
6 ZERO TRUST NETWORK ACCESS MARKET, BY OFFERING
- 6.1 INTRODUCTION
- 6.1.1 OFFERING: ZERO TRUST NETWORK ACCESS MARKET DRIVERS
- 6.2 SOLUTIONS
- 6.2.1 AGENT-BASED ZTNA
- 6.2.1.1 Robust endpoint posture enforcement and policy-driven compliance to fuel agent-based ZTNA adoption
- 6.2.2 AGENTLESS ZTNA
- 6.2.2.1 Simplifying secure access for distributed and BYOD environments
- 6.2.3 UNIVERSAL ZTNA
- 6.2.3.1 Enabling policy convergence across hybrid and multi-cloud environments
- 6.2.1 AGENT-BASED ZTNA
- 6.3 SERVICES
- 6.3.1 PROFESSIONAL SERVICES
- 6.3.1.1 Implementation & integration
- 6.3.1.1.1 Growing demand for seamless zero-trust deployment and interoperability with existing IT systems
- 6.3.1.2 Support & maintenance
- 6.3.1.2.1 Rising need for continuous platform stability and always-on assistance to ensure zero trust readiness
- 6.3.1.3 Consulting & advisory
- 6.3.1.3.1 Increasing reliance on expert guidance to design zero-trust strategies and compliance-driven frameworks
- 6.3.1.4 Training & education
- 6.3.1.4.1 Rising demand for workforce education to mitigate identity and access risks
- 6.3.1.1 Implementation & integration
- 6.3.2 MANAGED SERVICES
- 6.3.2.1 Growing demand for outsourced zero trust expertise to fuel ZTNA managed services adoption
- 6.3.1 PROFESSIONAL SERVICES
7 ZERO TRUST NETWORK ACCESS MARKET, BY DEPLOYMENT MODE
- 7.1 INTRODUCTION
- 7.1.1 DEPLOYMENT MODE: ZERO TRUST NETWORK ACCESS MARKET DRIVERS
- 7.2 CLOUD
- 7.2.1 SCALABILITY AND CLOUD-FIRST STRATEGIES DRIVING ADOPTION OF CLOUD-BASED DEPLOYMENTS
- 7.3 HYBRID
- 7.3.1 BALANCING LEGACY SYSTEM SUPPORT AND MODERN CLOUD SECURITY THROUGH HYBRID DEPLOYMENTS
8 ZERO TRUST NETWORK ACCESS MARKET, BY ORGANIZATION SIZE
- 8.1 INTRODUCTION
- 8.1.1 ORGANIZATION SIZE: ZERO TRUST NETWORK ACCESS MARKET DRIVERS
- 8.2 LARGE ENTERPRISES
- 8.2.1 SECURING GLOBAL OPERATIONS WITH ZERO TRUST NETWORK ACCESS
- 8.3 SMALL AND MEDIUM-SIZED ENTERPRISES (SMES)
- 8.3.1 CLOUD-FIRST STRATEGIES AND AFFORDABLE ZERO TRUST DRIVING SME ADOPTION
9 ZERO TRUST NETWORK ACCESS MARKET, BY APPLICATION AREA
- 9.1 INTRODUCTION
- 9.1.1 APPLICATION AREA: ZERO TRUST NETWORK ACCESS MARKET DRIVERS
- 9.2 REMOTE WORKFORCE ACCESS
- 9.2.1 SECURE REMOTE WORKFORCE ACCESS DRIVING ZERO TRUST NETWORK ACCESS ADOPTION
- 9.3 THIRD-PARTY/CONTRACTOR & BYOD ACCESS
- 9.3.1 ENABLING SECURE THIRD-PARTY AND BYOD ACCESS WITH AGENTLESS ZTNA
- 9.4 PRIVILEGED/ADMINISTRATIVE ACCESS
- 9.4.1 PROTECTING PRIVILEGED IDENTITIES THROUGH ZERO TRUST NETWORK ACCESS
- 9.5 SAAS APPLICATION ACCESS CONTROL
- 9.5.1 SECURING SAAS APPLICATIONS WITH IDENTITY-AWARE ZTNA
- 9.6 PRIVATE APPLICATION ACCESS
- 9.6.1 ENSURING SECURE ACCESS TO PRIVATE APPLICATIONS WITH ZTNA
- 9.7 WORKLOAD-TO-WORKLOAD & API ACCESS
- 9.7.1 IDENTITY AWARE SECURITY FOR WORKLOAD AND API ACCESS
10 ZERO TRUST NETWORK ACCESS MARKET, BY VERTICAL
- 10.1 INTRODUCTION
- 10.1.1 VERTICAL: ZERO TRUST NETWORK ACCESS MARKET DRIVERS
- 10.2 BFSI
- 10.2.1 STRINGENCY OF DATA PROTECTION AND DIGITAL BANKING GROWTH TO FUEL ZTNA ADOPTION
- 10.3 GOVERNMENT & PUBLIC SECTOR
- 10.3.1 ZERO TRUST ARCHITECTURE TO STRENGTHEN GOVERNMENT CYBER DEFENSES
- 10.4 RETAIL & E-COMMERCE
- 10.4.1 NEED FOR DATA SECURITY AND FRAUD PREVENTION TO DRIVE ZTNA ADOPTION
- 10.5 INFORMATION TECHNOLOGY (IT) & INFORMATION TECHNOLOGY-ENABLED SERVICES (ITES)
- 10.5.1 RISING DIGITALIZATION AND SUPPLY CHAIN RISKS DRIVING IT & ITES SECTOR TO EMBRACE ZTNA
- 10.6 HEALTHCARE
- 10.6.1 STRINGENT COMPLIANCE AND RISING ATTACKS TO DRIVE ZTNA ADOPTION
- 10.7 EDUCATION
- 10.7.1 FOCUS ON SECURE REMOTE LEARNING AND DATA PRIVACY TO DRIVE ZTNA ADOPTION
- 10.8 MANUFACTURING
- 10.8.1 INDUSTRY 4.0 AND CONNECTED OPERATIONS TO DRIVE ZTNA ADOPTION
- 10.9 OTHER VERTICALS
11 ZERO TRUST NETWORK ACCESS (ZTNA) MARKET, BY REGION
- 11.1 INTRODUCTION
- 11.2 NORTH AMERICA
- 11.2.1 NORTH AMERICA: ZERO TRUST NETWORK ACCESS MARKET DRIVERS
- 11.2.2 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 11.2.3 US
- 11.2.3.1 Surge in remote access needs and cybersecurity mandates to accelerate ZTNA adoption
- 11.2.4 CANADA
- 11.2.4.1 Digital transformation, evolving cyber threats, and regulatory mandates to fuel market growth
- 11.3 EUROPE
- 11.3.1 EUROPE: ZERO TRUST NETWORK ACCESS (ZTNA) MARKET DRIVERS
- 11.3.2 EUROPE: MACROECONOMIC OUTLOOK
- 11.3.3 UK
- 11.3.3.1 Stricter compliance mandates and identity-based threats to drive market
- 11.3.4 GERMANY
- 11.3.4.1 Rising hybrid work adoption and data protection mandates to accelerate demand for ZTNA
- 11.3.5 FRANCE
- 11.3.5.1 Stringent government regulations, remote work trends, and cloud adoption to propel market
- 11.3.6 ITALY
- 11.3.6.1 Surge in hybrid work, stringent compliance mandates, and rapid cloud adoption to accelerate ZTNA deployment
- 11.3.7 REST OF EUROPE
- 11.4 ASIA PACIFIC
- 11.4.1 ASIA PACIFIC: ZERO TRUST NETWORK ACCESS (ZTNA) MARKET DRIVERS
- 11.4.2 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 11.4.3 CHINA
- 11.4.3.1 Surge in digital transformation, strict cybersecurity laws, and complex IoT ecosystem to drive market
- 11.4.4 JAPAN
- 11.4.4.1 Rising breach sophistication and zero trust mandates to drive market
- 11.4.5 INDIA
- 11.4.5.1 Cloud-first strategies, fintech expansion, and regulatory compliance to fuel demand for ZTNA
- 11.4.6 REST OF ASIA PACIFIC
- 11.5 MIDDLE EAST & AFRICA
- 11.5.1 MIDDLE EAST & AFRICA: ZERO TRUST NETWORK (ZTNA) MARKET DRIVERS
- 11.5.2 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 11.5.3 GCC COUNTRIES
- 11.5.3.1 KSA
- 11.5.3.1.1 Stringent national cybersecurity regulations to drive market
- 11.5.3.2 UAE
- 11.5.3.2.1 Adaptive access controls and cloud-first mandates to drive market
- 11.5.3.3 Rest of GCC Countries
- 11.5.3.1 KSA
- 11.5.4 SOUTH AFRICA
- 11.5.4.1 Rising cyber risks and regulatory enforcement to drive market
- 11.5.5 REST OF MIDDLE EAST & AFRICA
- 11.6 LATIN AMERICA
- 11.6.1 LATIN AMERICA: ZERO TRUST NETWORK ACCESS (ZTNA) MARKET DRIVERS
- 11.6.2 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 11.6.3 BRAZIL
- 11.6.3.1 Rising cyber threats and regulatory pressure to fuel ZTNA adoption
- 11.6.4 MEXICO
- 11.6.4.1 Surge in cyberattacks and national cybersecurity strategy to accelerate ZTNA adoption
- 11.6.5 REST OF LATIN AMERICA
12 COMPETITIVE LANDSCAPE
- 12.1 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2020-2024
- 12.2 REVENUE ANALYSIS, 2020-2024
- 12.3 MARKET SHARE ANALYSIS, 2024
- 12.4 BRAND/PRODUCT COMPARISON
- 12.5 COMPANY VALUATION AND FINANCIAL METRICS
- 12.5.1 COMPANY VALUATION
- 12.5.2 FINANCIAL METRICS
- 12.6 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 12.6.1 STARS
- 12.6.2 EMERGING LEADERS
- 12.6.3 PERVASIVE PLAYERS
- 12.6.4 PARTICIPANTS
- 12.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 12.6.5.1 Company footprint
- 12.6.5.2 Regional footprint
- 12.6.5.3 Solution footprint
- 12.6.5.4 Vertical footprint
- 12.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 12.7.1 PROGRESSIVE COMPANIES
- 12.7.2 RESPONSIVE COMPANIES
- 12.7.3 DYNAMIC COMPANIES
- 12.7.4 STARTING BLOCKS
- 12.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 12.7.5.1 Detailed list of key startups/SMEs
- 12.7.5.2 Competitive benchmarking of key startups/SMEs
- 12.8 COMPETITIVE SCENARIO
- 12.8.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 12.8.2 DEALS
13 COMPANY PROFILE
- 13.1 INTRODUCTION
- 13.1.1 PALO ALTO NETWORKS
- 13.1.1.1 Business overview
- 13.1.1.2 Products/Solutions/Services offered
- 13.1.1.3 Recent developments
- 13.1.1.3.1 Product launches/enhancements
- 13.1.1.3.2 Deals
- 13.1.1.4 MnM view
- 13.1.1.4.1 Right to win
- 13.1.1.4.2 Strategic choices
- 13.1.1.4.3 Weaknesses and competitive threats
- 13.1.2 ZSCALER
- 13.1.2.1 Business overview
- 13.1.2.2 Products/Solutions/Services offered
- 13.1.2.3 Recent developments
- 13.1.2.3.1 Product launches/enhancements
- 13.1.2.3.2 Deals
- 13.1.2.4 MnM view
- 13.1.2.4.1 Right to win
- 13.1.2.4.2 Strategic choices
- 13.1.2.4.3 Weaknesses and competitive threats
- 13.1.3 CLOUDFLARE
- 13.1.3.1 Business overview
- 13.1.3.2 Products/Solutions/Services offered
- 13.1.3.3 Recent developments
- 13.1.3.3.1 Product launches/enhancements
- 13.1.3.3.2 Deals
- 13.1.3.4 MnM view
- 13.1.3.4.1 Right to win
- 13.1.3.4.2 Strategic choices
- 13.1.3.4.3 Weaknesses and competitive threats
- 13.1.4 CHECK POINT
- 13.1.4.1 Business overview
- 13.1.4.2 Products/Solutions/Services offered
- 13.1.4.3 Recent developments
- 13.1.4.3.1 Product launches/enhancements
- 13.1.4.3.2 Deals
- 13.1.4.3.3 Expansions
- 13.1.4.4 MnM view
- 13.1.4.4.1 Right to win
- 13.1.4.4.2 Strategic choices
- 13.1.4.4.3 Weaknesses and competitive threats
- 13.1.5 FORTINET
- 13.1.5.1 Business overview
- 13.1.5.2 Products/Solutions/Services offered
- 13.1.5.3 Recent developments
- 13.1.5.3.1 Product launches/enhancements
- 13.1.5.3.2 Deals
- 13.1.5.4 MnM view
- 13.1.5.4.1 Right to win
- 13.1.5.4.2 Strategic choices
- 13.1.5.4.3 Weaknesses and competitive threats
- 13.1.6 MICROSOFT
- 13.1.6.1 Business overview
- 13.1.6.2 Products/Solutions/Services offered
- 13.1.6.3 Recent developments
- 13.1.6.3.1 Product launches/enhancements
- 13.1.6.3.2 Deals
- 13.1.7 CISCO
- 13.1.7.1 Business overview
- 13.1.7.2 Products/Solutions/Services offered
- 13.1.7.3 Recent development
- 13.1.7.3.1 Product launches/enhancements
- 13.1.7.3.2 Deals
- 13.1.8 FORCEPOINT
- 13.1.8.1 Business overview
- 13.1.8.2 Products/Solutions/Services offered
- 13.1.8.3 Recent developments
- 13.1.8.3.1 Product launches/enhancements
- 13.1.8.3.2 Deals
- 13.1.9 TELEPORT
- 13.1.9.1 Business overview
- 13.1.9.2 Products/Solutions/Services offered
- 13.1.9.3 Recent developments
- 13.1.9.3.1 Product launches/enhancements
- 13.1.9.3.2 Deals
- 13.1.10 IVANTI
- 13.1.10.1 Business overview
- 13.1.10.2 Products/Solutions/Services offered
- 13.1.10.3 Recent developments
- 13.1.10.3.1 Product launches/enhancements
- 13.1.10.3.2 Deals
- 13.1.11 NETSKOPE
- 13.1.11.1 Business overview
- 13.1.11.2 Products/Solutions/Services offered
- 13.1.11.3 Recent developments
- 13.1.11.3.1 Product launches/enhancements
- 13.1.11.3.2 Deals
- 13.1.12 IBOSS
- 13.1.12.1 Business overview
- 13.1.12.2 Products/Solutions/Services offered
- 13.1.12.3 Recent developments
- 13.1.12.3.1 Product launches/enhancements
- 13.1.12.3.2 Deals
- 13.1.13 APPGATE
- 13.1.13.1 Business overview
- 13.1.13.2 Products/Solutions/Services offered
- 13.1.13.3 Recent developments
- 13.1.13.3.1 Product launches/enhancements
- 13.1.13.3.2 Deals
- 13.1.14 FORTRA
- 13.1.14.1 Business overview
- 13.1.14.2 Products/Solutions/Services offered
- 13.1.14.3 Recent developments
- 13.1.14.3.1 Product launches/enhancements
- 13.1.14.3.2 Deals
- 13.1.15 BROADCOM
- 13.1.15.1 Business overview
- 13.1.15.2 Products/Solutions/Services offered
- 13.1.15.3 Recent developments
- 13.1.15.3.1 Product launches/enhancements
- 13.1.15.3.2 Deals
- 13.1.16 CITRIX
- 13.1.17 SOPHOS
- 13.1.18 AKAMAI
- 13.1.19 SONICWALL
- 13.1.20 MENLO SECURITY
- 13.1.21 CLOUDBRINK
- 13.1.22 VERSA NETWORKS
- 13.1.23 NETFOUNDRY
- 13.1.24 JAMF
- 13.1.25 DEFENSX
- 13.1.26 ALKIRA
- 13.1.27 XAGE SECURITY
- 13.1.28 HILLSTONE NETWORKS
- 13.1.29 SYSTANCIA
- 13.1.30 ACCOPS
- 13.1.1 PALO ALTO NETWORKS
14 ADJACENT MARKETS
- 14.1 INTRODUCTION TO ADJACENT MARKETS
- 14.2 LIMITATIONS
- 14.3 ADJACENT MARKETS
- 14.3.1 SECURE ACCESS SERVICE EDGE (SASE) MARKET
- 14.3.2 SECURITY SERVICE EDGE (SSE) MARKET
15 APPENDIX
- 15.1 DISCUSSION GUIDE
- 15.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 15.3 CUSTOMIZATION OPTIONS
- 15.4 RELATED REPORTS
- 15.5 AUTHOR DETAILS



















