
|
시장보고서
상품코드
1819090
생성형 AI 사이버 보안 시장 : 생성형 AI 기반 사이버 보안별, 생성형 AI용 사이버 보안 소프트웨어별, 보안 유형별 - 예측(-2031년)Generative AI Cybersecurity Market by Generative AI-based Cybersecurity (SIEM, Risk Assessment, Threat Intelligence), Cybersecurity Software for Generative AI (AI Model Security), Security Type (Data Encryption, Access Control) - Global Forecast to 2031 |
||||||
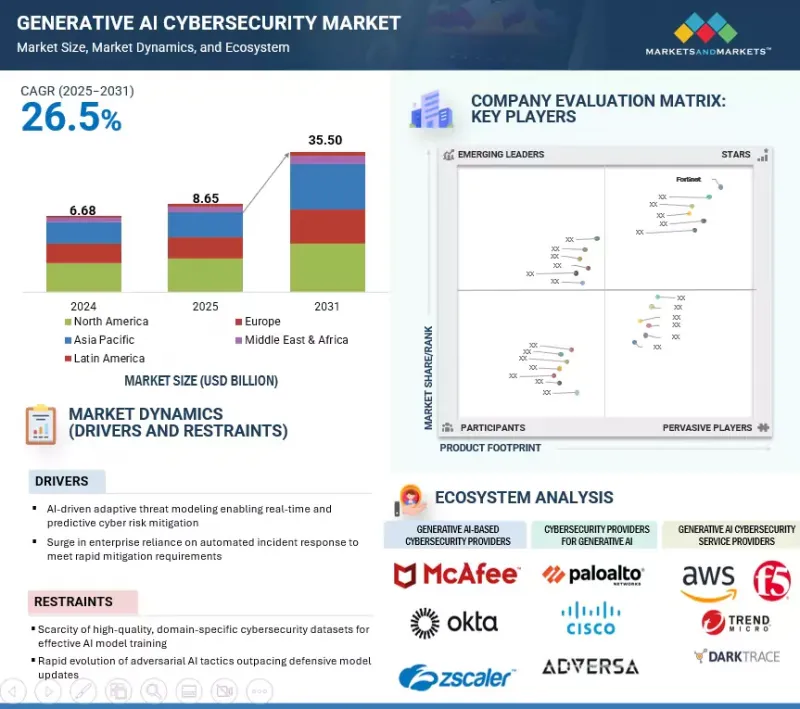
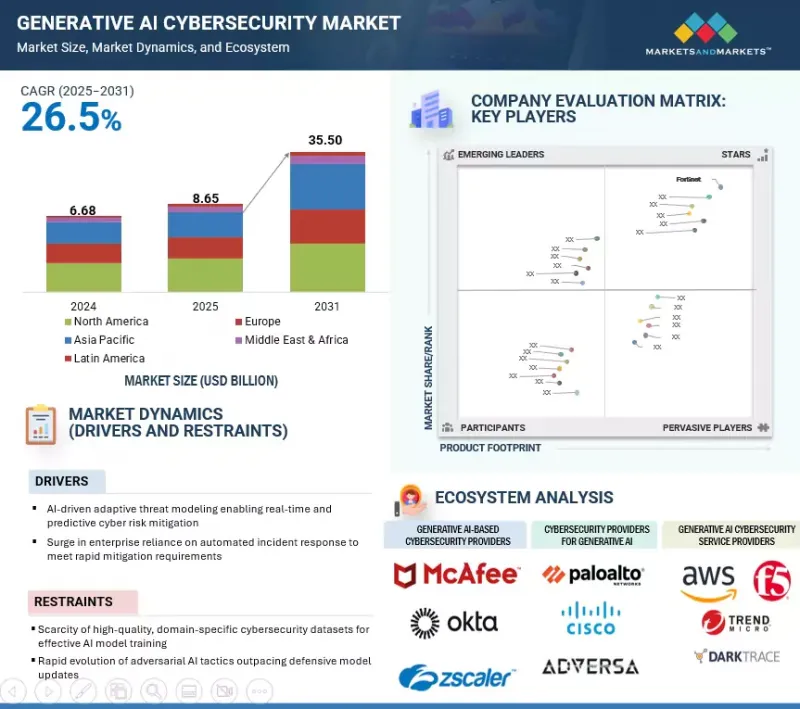
세계의 생성형 AI 사이버 보안 시장 규모는 2025년 추정 86억 5,000만 달러에서 2031년까지 355억 달러에 달할 것으로 예측되며, 예측 기간에 CAGR로 26.5%의 성장이 전망됩니다.
시장 촉진요인은 타사 모델 리포지토리, API, 플러그인을 대상으로 한 AI 공급망 공격이 증가하고 있으며, 이로 인해 기업들은 AI 자산을 보호하기 위해 모델 출처 검증과 코드 서명을 채택하고 있습니다.
| 조사 범위 | |
|---|---|
| 조사 대상 연도 | 2020-2031년 |
| 기준 연도 | 2024년 |
| 예측 기간 | 2025-2031년 |
| 단위 | 100만 달러 |
| 부문 | 제공, 생성형 AI 기반 사이버 보안 소프트웨어, 생성형 AI용 사이버 보안 소프트웨어, 보안 유형, 최종사용자, 지역 |
| 대상 지역 | 북미, 유럽, 아시아태평양, 중동 및 아프리카, 라틴아메리카 |
또한, 멀티테넌트 클라우드 환경에서 서비스형 모델(model-as-a-service)의 사용이 확대됨에 따라 기밀 컴퓨팅과 기밀성이 높은 AI 워크로드를 보호하기 위한 보안 인클로브 실행에 대한 수요가 증가하고 있습니다. 그러나 악의적인 행위자가 생성형 AI를 악용하여 피싱 캠페인 자동화, 딥페이크 생성, 지능형 악성코드 개발 등에 악용하고 있기 때문에 시장은 큰 제약요인에 직면해 있습니다. 이러한 이중용도의 도전으로 인해 벤더들은 혁신과 보안의 균형을 유지하면서 적대적인 AI 위협에 한발 앞서 대응할 수 있는 방어 전략을 지속적으로 발전시켜야 합니다.
"위험 평가 소프트웨어가 성장을 주도하고, 예방적 위협 완화를 촉진하고 있습니다."
생성형 AI 사이버 보안 생태계 내 위험 평가 소프트웨어는 위협 예방 및 컴플라이언스 중심의 의사결정에 있어 중요한 역할을 수행하기 때문에 예측 기간 동안 가장 높은 CAGR을 기록할 것으로 예상됩니다. 생성형 AI는 복잡한 공격 시나리오를 시뮬레이션하고, 상호연결된 시스템 전체에 미치는 영향을 예측하며, 기존 툴이 간과할 수 있는 잠재적 취약점을 식별하여 기존 위험 평가를 강화합니다. 이 기술은 실시간 텔레메트리, 위협 인텔리전스 피드, 컨텍스트 기반 비즈니스 영향을 기반으로 사이버 위험을 지속적이고 적응적으로 점수화하여 기업이 복구 작업의 우선순위를 정확하게 결정할 수 있도록 지원합니다. 미국 SEC의 사이버 사고 공개 규정과 EU의 디지털 운영 탄력성 법(Digital Operational Resilience Act, DORA)과 같은 진화하는 규제에 대한 기대에 부응하기 위해 BFSI, 의료, 중요 인프라와 같이 엄격한 컴플라이언스 프레임워크를 가진 산업에서 채택이 가속화되고 있습니다. 또한, AI 기반 위험 평가 플랫폼은 SOAR(Security Orchestration, Automation, and Response) 시스템과 통합되어 정책 적용을 자동화하고 사고 발생 시 의사결정 대기 시간을 단축하고 있습니다. 벤더는 생성 모델을 활용하여 동적 환경의 리스크를 평가함으로써 보안 태세와 업무 복원력을 크게 향상시킬 수 있는 예측적 인사이트를 제공할 수 있습니다. 규제 당국의 압력, 업무 효율성 향상, 사이버 리스크를 비즈니스 용어로 정량화하여 전달할 수 있는 능력이 결합되어 이 소프트웨어 부문은 지속적으로 높은 성장세를 보이고 있습니다.
"AI 중심의 코드 보안이 미션 크리티컬하게 되면서 정적 애플리케이션 보안 테스트가 가장 큰 시장 규모를 차지합니다."
정적 애플리케이션 보안 테스트(SAST)는 AI를 통합한 소프트웨어 개발 파이프라인의 안전을 보장하고 배포 전 코드 무결성을 보장하는 데 중요한 역할을 하기 때문에 2025년 애플리케이션 보안 유형 중 가장 큰 시장 점유율을 차지할 것으로 예상됩니다. 기업 AI 이니셔티브에서 보안 바이 디자인 원칙의 채택이 증가함에 따라, SAST는 컴플라이언스 중심의 대책에서 전략적 필수품으로 격상되고 있습니다. 특히 규제 기관이 민감한 데이터를 다루는 AI 지원 애플리케이션에 대한 감시를 강화하고 있기 때문입니다. 동적 테스트와 달리 SAST는 소스 코드 수준에서 취약점을 조기에 발견할 수 있어 수정 비용을 크게 줄이고, 악용된 결함이 프로덕션 환경에 도달할 위험을 최소화할 수 있습니다. BFSI, 의료, 정부 기관 등 AI 애플리케이션이 고가의 규제 데이터를 처리하는 분야에서는 생성형 AI의 배포와 함께 SAST의 도입이 가속화되고 있으며, 인젝션 공격, 안전하지 않은 종속성, 코드 레벨의 데이터 유출에 대한 강력한 보호를 보장합니다.
세계의 생성형 AI 사이버 보안 시장에 대해 조사 분석했으며, 주요 촉진요인과 억제요인, 경쟁 상황, 향후 동향 등의 정보를 전해드립니다.
목차
제1장 소개
제2장 조사 방법
제3장 주요 요약
제4장 중요한 인사이트
- 생성형 AI 사이버 보안 시장의 매력적인 기회
- 생성형 AI 사이버 보안 시장 : 상위 3개 보안 유형
- 북미의 생성형 AI 사이버 보안 시장 : 제공별, 보안 유형별
- 생성형 AI 사이버 보안 시장 : 지역별
제5장 시장 개요와 산업 동향
- 소개
- 시장 역학
- 성장 촉진요인
- 성장 억제요인
- 기회
- 과제
- 생성형 AI 사이버 보안의 진화
- 공급망 분석
- 생태계 분석
- 생성형 AI 기반 사이버 보안 프로바이더
- 생성형 AI용 사이버 보안 프로바이더
- 생성형 AI 사이버 보안 서비스 프로바이더
- 보안 종류
- 투자와 자금 조달 시나리오
- 사례 연구 분석
- 기술 분석
- 주요 기술
- 보완 기술
- 인접 기술
- 규제 상황
- 규제기관, 정부기관, 기타 조직
- 주요 규제
- 특허 분석
- 조사 방법
- 특허 출원 건수 : 서류 유형별
- 혁신과 특허 출원
- 가격 책정 분석
- 주요 기업 평균판매가격 : 제공별(2025년)
- 평균판매가격 : 증권 종별(2025년)
- 주요 회의와 이벤트(2025-2026년)
- Porter's Five Forces 분석
- 주요 이해관계자와 구입 기준
- 고객 비즈니스에 영향을 미치는 동향/혼란
제6장 생성형 AI 사이버 보안 시장 : 제공별
- 소개
- 소프트웨어 : 유형별
- 특정 용도용 소프트웨어에 의한 생성형 AI 보안 강화
- 생성형 AI 기반 사이버 보안 소프트웨어
- 생성형 AI용 사이버 보안 소프트웨어
- 소프트웨어 : 전개 방식별
- 유연한 전개 방식에 의한 사이버 방어 최적화
- 클라우드
- 온프레미스
- 서비스
- 종합적인 서비스를 통해 실현되는 탄력적인 생성형 AI 사이버 보안
- 전문 서비스
- 매니지드 서비스
제7장 생성형 AI용 사이버 보안 소프트웨어 시장 : 유형별
- 소개
- 생성형 AI 트레이닝 데이터 보안 소프트웨어
- 생성형 AI 모델 보안 소프트웨어
- 생성형 AI 인프라 보안 소프트웨어
- 생성형 AI 애플리케이션 보안 소프트웨어
제8장 생성형 AI 사이버 보안 시장 : 최종사용자별
- 소개
- 최종사용자 : 생성형 AI 기반 사이버 보안
- 생성형 AI에 의한 첨단 위협 경감 추진
- 정부·방위
- BFSI
- IT·ITeS
- 헬스케어·생명과학
- 소매·E-Commerce
- 제조
- 에너지·유틸리티
- 통신
- 자동차·운송·물류
- 미디어·엔터테인먼트
- 기타 최종사용자
- 최종사용자 : 생성형 AI용 사이버 보안
- 최종사용자를 지키기 위한 생성형 AI 서비스 보호
- 클라우드 하이퍼스케일러
- 매니지드 보안 서비스 프로바이더
- 생성형 AI 프로바이더
제9장 생성형 AI 기반 사이버 보안 소프트웨어 시장 : 유형별
- 소개
- 위협 탐지·인텔리전스 소프트웨어
- 리스크 평가 소프트웨어
- 노출 관리 소프트웨어
- 피싱 시뮬레이션·방지 소프트웨어
- 수복 가이던스 소프트웨어
- 위협 사냥 플랫폼
- 코드 분석 소프트웨어
제10장 생성형 AI 사이버 보안 시장 : 보안 유형별
- 소개
- 데이터베이스 보안
- 네트워크 보안
- 엔드포인트 보안
- 애플리케이션 보안
제11장 생성형 AI 사이버 보안 시장 : 지역별
- 소개
- 북미
- 북미의 생성형 AI 사이버 보안 시장 촉진요인
- 북미의 거시경제 전망
- 미국
- 캐나다
- 유럽
- 유럽의 생성형 AI 사이버 보안 시장 촉진요인
- 유럽의 거시경제 전망
- 영국
- 독일
- 프랑스
- 기타 유럽
- 아시아태평양
- 아시아태평양의 생성형 AI 사이버 보안 시장 촉진요인
- 아시아태평양의 거시경제 전망
- 중국
- 인도
- 일본
- 기타 아시아태평양
- 중동 및 아프리카
- 중동 및 아프리카의 생성형 AI 사이버 보안 시장 촉진요인
- 중동 및 아프리카의 거시경제 전망
- 사우디아라비아
- 아랍에미리트
- 기타 중동
- 아프리카
- 라틴아메리카
- 라틴아메리카의 생성형 AI 사이버 보안 시장 촉진요인
- 라틴아메리카의 거시경제 전망
- 브라질
- 멕시코
- 기타 라틴아메리카
제12장 경쟁 구도
- 개요
- 주요 진출 기업의 전략
- 매출 분석
- 시장 점유율 분석
- 제품의 비교 분석
- 제품의 비교 분석 : 생성형 AI 기반 사이버 보안
- 제품의 비교 분석 : 생성형 AI용 사이버 보안
- 기업 평가와 재무 지표
- 기업 평가 매트릭스 : 주요 기업(2024년)
- 기업 평가 매트릭스 : 스타트업/중소기업(2024년)
- 경쟁 시나리오와 동향
제13장 기업 개요
- 소개
- 생성형 AI 기반 사이버 보안 솔루션 프로바이더
- MICROSOFT
- IBM
- SENTINELONE
- NVIDIA
- NEURALTRUST
- TREND MICRO
- BLACKBERRY
- OKTA
- SANGFOR TECHNOLOGIES
- VERACODE
- LEXISNEXIS
- SECURITYSCORECARD
- BROADCOM
- COHESITY
- ELASTIC NV
- CYBEREASON
- FLASHPOINT
- MOSTLY AI
- RECORDED FUTURE
- SECUREFRAME
- SLASHNEXT
- VIRUSTOTAL
- XENONSTACK
- ZEROFOX
- 생성형 AI용 사이버 보안 솔루션 프로바이더
- AWS
- CISCO
- CROWDSTRIKE
- FORTINET
- ZSCALER
- PALO ALTO NETWORKS
- DARKTRACE
- F5
- SOPHOS
- TRELLIX
- TENABLE
- SNYK
- ABNORMAL SECURITY
- ADVERSA AI
- AQUA SECURITY
- BIGID
- CHECKMARX
- CREDO AI
- DEEPKEEP
- LAKERA
- SKYFLOW
- TROJAI
제14장 인접 시장과 관련 시장
- 소개
- 생성형 AI 시장 - 세계의 예측(-2032년)
- 시장 정의
- 시장 개요
- 사이버 보안용 AI 시장 - 세계의 예측(-2028년)
- 시장 정의
- 시장 개요
제15장 부록
KSM 25.09.29The generative AI cybersecurity market is anticipated to witness a compound annual growth rate (CAGR) of 26.5% over the forecast period, reaching USD 35.50 billion by 2031 from an estimated USD 8.65 billion in 2025. The market is driven by the rise in AI supply chain attacks targeting third-party model repositories, APIs, and plugins, which is pushing enterprises to adopt model provenance verification and code signing to secure AI assets.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2020-2031 |
| Base Year | 2024 |
| Forecast Period | 2025-2031 |
| Units Considered | USD (Million) |
| Segments | Offering, Generative AI-based Cybersecurity Software, Cybersecurity Software for Generative AI, Security Type, End User, and Region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
Additionally, the growing use of model-as-a-service in multi-tenant cloud environments is increasing demand for confidential computing and secure enclave execution to protect sensitive AI workloads. However, the market also faces a significant restraint as malicious actors exploit generative AI to automate phishing campaigns, create deepfakes, and develop advanced malware. This dual-use challenge forces vendors to continually evolve defensive strategies to stay ahead of adversarial AI threats while balancing innovation and security.
"Risk assessment software leads growth, driving proactive threat mitigation"
Risk assessment software within the generative AI cybersecurity ecosystem is projected to record the highest CAGR over the forecast period, fueled by its critical role in proactive threat prevention and compliance-driven decision-making. Generative AI enhances traditional risk assessment by simulating complex attack scenarios, predicting cascading impacts across interconnected systems, and identifying latent vulnerabilities that conventional tools may overlook. The technology enables continuous, adaptive scoring of cyber risks based on real-time telemetry, threat intelligence feeds, and contextual business impact, allowing enterprises to prioritize remediation efforts with precision. Industries with stringent compliance frameworks, such as BFSI, healthcare, and critical infrastructure, are accelerating adoption to meet evolving regulatory expectations like the US SEC's cyber incident disclosure rules and the EU Digital Operational Resilience Act (DORA). Moreover, AI-driven risk assessment platforms are being integrated with Security Orchestration, Automation, and Response (SOAR) systems to automate policy enforcement and reduce decision latency during incidents. By leveraging generative models to evaluate risks in dynamic environments, vendors can offer predictive insights that materially improve security posture and operational resilience. The combination of regulatory pressure, operational efficiency gains, and the ability to quantify and communicate cyber risk in business terms positions this software segment for sustained high-growth momentum.
"Static application security testing to hold largest market as AI-centric code security becomes mission-critical"
Static Application Security Testing (SAST) is estimated to capture the largest market share within application security types in 2025, driven by its critical role in securing AI-integrated software development pipelines and ensuring code integrity before deployment. The increasing adoption of secure-by-design principles in enterprise AI initiatives has elevated SAST from a compliance-focused measure to a strategic necessity, especially as regulatory bodies tighten oversight on AI-enabled applications handling sensitive data. Unlike dynamic testing, SAST enables early detection of vulnerabilities at the source code level, significantly reducing remediation costs and minimizing the risk of exploited flaws reaching production environments. In sectors such as BFSI, healthcare, and government, where AI applications process high-value and regulated data, SAST adoption is accelerating in parallel with generative AI deployments, ensuring robust protection against injection attacks, insecure dependencies, and code-level data leaks. Moreover, the growing integration of AI coding assistants and automated DevSecOps pipelines is expanding the demand for SAST tools capable of handling AI-generated code, addressing unique vulnerabilities introduced by large language model-assisted programming. Leading security vendors are embedding AI-driven analytics into SAST platforms to improve vulnerability prioritization and reduce false positives, further enhancing operational efficiency and developer adoption. These combined factors position SAST as the dominant force in the 2025 application security landscape.
"Asia Pacific to witness rapid market growth fueled by innovation and emerging technologies, while North America leads in market size"
North America is estimated to account for the largest share of the generative AI cybersecurity market in 2025, underpinned by its mature technology ecosystem, strong enterprise adoption rates, and early regulatory engagement in AI governance. The region benefits from the presence of leading cybersecurity vendors, robust venture capital activity, and a concentration of high-value industries such as BFSI, healthcare, and defense, where AI-driven security solutions are rapidly embedded into operational frameworks. Government-backed initiatives, such as the US Executive Order on AI and sector-specific compliance mandates, are accelerating investment in advanced AI threat detection, incident response automation, and AI-assisted risk assessment platforms. In parallel, Asia Pacific is poised to record the fastest CAGR during the forecast period, driven by rapid digital transformation, large-scale cloud adoption, and a growing need to counter evolving cyber threats targeting expanding digital infrastructures. Countries such as China, India, Japan, and South Korea are investing heavily in AI R&D, supported by government programs and strategic public-private partnerships. The region's expanding base of SMEs and startups is leveraging generative AI for both offensive and defensive cybersecurity innovation, while hyperscale cloud providers are localizing AI security services to address diverse compliance environments. This combination of high-growth adoption patterns in the Asia Pacific and entrenched market dominance in North America is shaping a dual-center growth model for the global generative AI cybersecurity landscape.
Breakdown of Primaries
In-depth interviews were conducted with Chief Executive Officers (CEOs), innovation and technology directors, system integrators, and executives from various key organizations operating in the generative AI cybersecurity market.
- By Company: Tier I - 35%, Tier II - 45%, and Tier III - 20%
- By Designation: C Level - 35%, Director Level - 25%, and others - 40%
- By Region: North America - 42%, Europe - 20%, Asia Pacific - 25%, Middle East & Africa - 8%, and Latin America - 5%
The report includes the study of key players offering generative AI cybersecurity solutions and services. It profiles major vendors in the generative AI cybersecurity market. The major market players include Microsoft (US), IBM (US), Google (US), SentinelOne (US), AWS (US), NVIDIA (US), Cisco (US), CrowdStrike (US), Fortinet (US), Zscaler (US), Trend Micro (Japan), Palo Alto Networks (US), BlackBerry (Canada), Darktrace (UK), F5 (US), Okta (US), Sangfor (China), SecurityScorecard (US), Sophos (UK), Broadcom (US), Trellix (US), Veracode (US), LexisNexis (US), Abnormal Security (US), Adversa AI (Israel), Aquasec (US), BigID (US), Checkmarx (US), Cohesity (US), Credo AI (US), NeuralTrust (Spain), Cybereason (US), DeepKeep (Israel), Elastic NV (US), Flashpoint (US), Lakera (US), MOSTLY AI (Austria), Recorded Future (US), Secureframe (US), Skyflow (US), SlashNext (US), Snyk (US), Tenable (US), TrojAI (Canada), VirusTotal (Spain), XenonStack (UAE), and Zerofox (US).
Research Coverage
This research report covers the generative AI cybersecurity market, which has been segmented based on offering, generative AI-based cybersecurity software, cybersecurity software for generative AI, security type, and end user. The offering segment consists of software and services. The generative AI-based cybersecurity solutions segment consists of threat detection & intelligence software, risk assessment software, exposure management software, phishing simulation & prevention software, remediation guidance software, threat hunting platforms, and code analysis software. The cybersecurity solutions for the generative AI segment include generative AI training data security software, generative AI model security software, generative AI infrastructure security software, and generative AI application security software. The security type segment consists of generative AI training data security software, generative AI model security software, generative AI infrastructure security software, and generative AI application security software. The end user segment consists of generative AI-based cybersecurity end users and cybersecurity for generative AI end users. The regional analysis of the generative AI cybersecurity market covers North America, Europe, Asia Pacific, the Middle East & Africa (MEA), and Latin America.
Key Benefits of Buying the Report
The report would provide the market leaders/new entrants in this market with information on the closest approximations of the revenue numbers for the overall generative AI cybersecurity market and its subsegments. It would help stakeholders understand the competitive landscape and gain more insights to position their business and plan suitable go-to-market strategies. It also helps stakeholders understand the market's pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights on the following pointers:
Analysis of key drivers (Rising frequency and sophistication of AI-driven cyberattacks accelerating adoption of AI-powered defense tools, Operational efficiency gains through AI-assisted Security Operations Centers (AI-SOC) reducing alert fatigue and response times, Escalating zero-day vulnerabilities necessitating rapid AI-enabled detection and remediation, and Growing demand for AI-powered behavioral anomaly detection to combat insider threats), restraints (Lack of standardized benchmarks for evaluating AI cybersecurity solutions, and Uncertainty around liability in AI-led automated security actions), opportunities (Adoption of Zero Trust for AI frameworks for validating AI-generated outputs, Leveraging AI for real-time detection of adversarial AI attacks on critical infrastructure, and Development of AI-driven penetration testing and vulnerability assessment platforms), and challenges (Exploitation of prompt injection and model manipulation techniques to bypass safeguards, and Growth of AI-enabled deepfake fraud targeting enterprises and critical infrastructure).
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the generative AI cybersecurity market.
- Market Development: Comprehensive information about lucrative markets - the report analyses the generative AI cybersecurity market across varied regions.
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the generative AI cybersecurity market.
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and offerings of leading players like Microsoft (US), IBM (US), Google (US), SentinelOne (US), AWS (US), NVIDIA (US), Cisco (US), CrowdStrike (US), Fortinet (US), Zscaler (US), Trend Micro (Japan), Palo Alto Networks (US), BlackBerry (Canada), Darktrace (UK), F5 (US), Okta (US), Sangfor (China), SecurityScorecard (US), Sophos (UK), Broadcom (US), Trellix (US), Veracode (US), LexisNexis (US), Abnormal Security (US), Adversa AI (Israel), Aquasec (US), BigID (US), Checkmarx (US), Cohesity (US), Credo AI (US), NeuralTrust (Spain), Cybereason (US), DeepKeep (Israel), Elastic NV (US), Flashpoint (US), Lakera (US), MOSTLY AI (Austria), Recorded Future (US), Secureframe (US), Skyflow (US), SlashNext (US), Snyk (US), Tenable (US), TrojAI (Canada), VirusTotal (Spain), XenonStack (UAE), and Zerofox (US), among others, in the generative AI cybersecurity market. The report also helps stakeholders understand the pulse of the market and provides them with information on key market drivers, restraints, challenges, and opportunities.
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 OBJECTIVES OF THE STUDY
- 1.2 MARKET DEFINITION AND SCOPE
- 1.3 MARKET SCOPE
- 1.3.1 MARKET SEGMENTATION
- 1.3.2 INCLUSIONS AND EXCLUSIONS
- 1.3.3 YEARS CONSIDERED
- 1.4 CURRENCY CONSIDERED
- 1.5 STAKEHOLDERS
- 1.6 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 List of primary participants
- 2.1.2.2 Breakdown of primaries
- 2.1.2.3 Key industry insights
- 2.2 DATA TRIANGULATION
- 2.3 MARKET SIZE ESTIMATION
- 2.3.1 TOP-DOWN APPROACH
- 2.3.2 BOTTOM-UP APPROACH
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES IN GENERATIVE AI CYBERSECURITY MARKET
- 4.2 GENERATIVE AI CYBERSECURITY MARKET: TOP THREE SECURITY TYPES
- 4.3 NORTH AMERICA: GENERATIVE AI CYBERSECURITY MARKET, BY OFFERING AND SECURITY TYPE
- 4.4 GENERATIVE AI CYBERSECURITY MARKET, BY REGION
5 MARKET OVERVIEW AND INDUSTRY TRENDS
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Rising frequency and sophistication of AI-driven cyberattacks
- 5.2.1.2 Operational efficiency gains through AI-assisted Security Operations Centers (AI-SOC), reducing alert fatigue and response times
- 5.2.1.3 Escalating zero-day vulnerabilities, necessitating rapid AI-enabled detection and remediation
- 5.2.1.4 Growing demand for AI-powered behavioral anomaly detection to combat insider threats
- 5.2.2 RESTRAINTS
- 5.2.2.1 Lack of standardized benchmarks for evaluation of AI cybersecurity solutions
- 5.2.2.2 Uncertainty around liability in AI-led automated security actions
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Adoption of Zero Trust for AI frameworks to validate AI-generated outputs
- 5.2.3.2 Leveraging AI for real-time detection of adversarial AI attacks on critical infrastructure
- 5.2.3.3 Development of AI-driven penetration testing and vulnerability assessment platforms
- 5.2.4 CHALLENGES
- 5.2.4.1 Exploitation of prompt injection and model manipulation techniques to bypass safeguards
- 5.2.4.2 Proliferation of AI-enabled deepfake fraud targeting enterprises and critical infrastructure
- 5.2.1 DRIVERS
- 5.3 EVOLUTION OF GENERATIVE AI CYBERSECURITY
- 5.4 SUPPLY CHAIN ANALYSIS
- 5.5 ECOSYSTEM ANALYSIS
- 5.5.1 GENERATIVE AI-BASED CYBERSECURITY PROVIDERS
- 5.5.2 CYBERSECURITY PROVIDERS FOR GENERATIVE AI
- 5.5.3 GENERATIVE AI CYBERSECURITY SERVICE PROVIDERS
- 5.5.4 SECURITY TYPES
- 5.6 INVESTMENT AND FUNDING SCENARIO
- 5.7 CASE STUDY ANALYSIS
- 5.7.1 ZEROFOX PROVIDES ACTIONABLE INTELLIGENCE TO SHORE UP SIMPLY BUSINESS'S INFORMATION SECURITY
- 5.7.2 POMELO STAYS SECURE AMIDST RAPID GROWTH WITH SNYK
- 5.7.3 EVOCABANK HELPS NOKIA PROTECT MILLIONS OF FOLLOWERS
- 5.7.4 CARNIVAL CORPORATION CHARTS A SAFER COURSE WITH CYBERARK
- 5.7.5 IBM USES PALO ALTO TO PROTECTS ITS AI SYSTEMS
- 5.7.6 OPENAI USES OKTA TO SAFEGUARD ITSELF
- 5.8 TECHNOLOGY ANALYSIS
- 5.8.1 KEY TECHNOLOGIES
- 5.8.1.1 Adversarial machine learning
- 5.8.1.2 Federated learning security
- 5.8.1.3 Differential privacy
- 5.8.1.4 Homomorphic encryption
- 5.8.1.5 Secure multi-party computation
- 5.8.2 COMPLEMENTARY TECHNOLOGIES
- 5.8.2.1 Blockchain
- 5.8.2.2 Zero trust architecture
- 5.8.2.3 Endpoint detection & response
- 5.8.2.4 Vulnerability management
- 5.8.3 ADJACENT TECHNOLOGIES
- 5.8.3.1 Quantum computing
- 5.8.3.2 DevSecOps
- 5.8.3.3 Forensics & incident response
- 5.8.3.4 Big data analytics
- 5.8.1 KEY TECHNOLOGIES
- 5.9 REGULATORY LANDSCAPE
- 5.9.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 5.9.2 KEY REGULATIONS
- 5.9.2.1 North America
- 5.9.2.1.1 Executive Order on AI (US)
- 5.9.2.1.2 NIST AI Risk Management Framework (under the NDAA)
- 5.9.2.1.3 National AI Risk Management Framework
- 5.9.2.1.4 Artificial Intelligence and Data Act (AIDA)
- 5.9.2.1.5 Kids Online Safety Act (KOSA)
- 5.9.2.1.6 Canadian Centre for Cyber Security
- 5.9.2.1.7 Privacy Guidelines
- 5.9.2.2 Europe
- 5.9.2.2.1 Regulation (EU) 2024/1689 - Artificial Intelligence Act (AI Act)
- 5.9.2.2.2 Directive (EU) 2022/2555 - NIS 2 Directive
- 5.9.2.2.3 Regulation (EU) 2024/2847 - Cyber Resilience Act (CRA)
- 5.9.2.2.4 Regulation (EU) 2024/903 - Cyber Solidarity Act (CSA)
- 5.9.2.3 Asia Pacific
- 5.9.2.3.1 Model AI Governance Framework (Singapore)
- 5.9.2.3.2 AI Guidelines for Business Version 1.0 (Japan)
- 5.9.2.3.3 Basic Law for Promoting Responsible AI (Japan, proposed)
- 5.9.2.3.4 Act on Promotion of the AI Industry and Framework for Establishing Trustworthy AI (South Korea)
- 5.9.2.4 Middle East & Africa
- 5.9.2.4.1 UAE Strategy for Artificial Intelligence 2031
- 5.9.2.4.2 National AI Programme
- 5.9.2.4.3 African Union Convention on Cyber Security and Personal Data Protection (Malabo Convention)
- 5.9.2.4.4 National Strategy for Data and AI (NSDAI)
- 5.9.2.4.5 Saudi Data and Artificial Intelligence Authority (SDAIA)
- 5.9.2.5 Latin America
- 5.9.2.5.1 Bill No. 2,338/2023 - Proposed Law on Artificial Intelligence (Brazil)
- 5.9.2.5.2 National Artificial Intelligence Strategy (EBIA) (Brazil)
- 5.9.2.5.3 National Policy on Exploitation of Data (Big Data) (Colombia)
- 5.9.2.5.4 AI Regulation Bill (Colombia)
- 5.9.2.1 North America
- 5.10 PATENT ANALYSIS
- 5.10.1 METHODOLOGY
- 5.10.2 PATENTS FILED, BY DOCUMENT TYPE
- 5.10.3 INNOVATION AND PATENT APPLICATIONS
- 5.11 PRICING ANALYSIS
- 5.11.1 AVERAGE SELLING PRICE OF KEY PLAYERS, BY OFFERING, 2025
- 5.11.2 AVERAGE SELLING PRICE, BY SECURITY TYPE, 2025
- 5.12 KEY CONFERENCES AND EVENTS (2025-2026)
- 5.13 PORTER'S FIVE FORCES ANALYSIS
- 5.13.1 THREAT OF NEW ENTRANTS
- 5.13.2 THREAT OF SUBSTITUTES
- 5.13.3 BARGAINING POWER OF SUPPLIERS
- 5.13.4 BARGAINING POWER OF BUYERS
- 5.13.5 INTENSITY OF COMPETITION RIVALRY
- 5.14 KEY STAKEHOLDERS & BUYING CRITERIA
- 5.14.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 5.14.2 BUYING CRITERIA
- 5.15 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.15.1 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
6 GENERATIVE AI CYBERSECURITY MARKET, BY OFFERING
- 6.1 INTRODUCTION
- 6.1.1 OFFERING: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 6.2 SOFTWARE, BY TYPE
- 6.2.1 STRENGTHENING OF GENERATIVE AI SECURITY WITH PURPOSE-BUILT SOFTWARE
- 6.2.2 GENERATIVE AI-BASED CYBERSECURITY SOFTWARE
- 6.2.3 CYBERSECURITY SOFTWARE FOR GENERATIVE AI
- 6.3 SOFTWARE, BY DEPLOYMENT MODE
- 6.3.1 OPTIMIZING CYBER DEFENSE WITH FLEXIBLE DEPLOYMENT MODES
- 6.3.2 CLOUD
- 6.3.3 ON-PREMISES
- 6.4 SERVICES
- 6.4.1 RESILIENT GENERATIVE AI CYBERSECURITY ENABLED THROUGH COMPREHENSIVE SERVICES
- 6.4.2 PROFESSIONAL SERVICES
- 6.4.2.1 Training & consulting
- 6.4.2.2 System integration & implementation
- 6.4.2.3 Support & maintenance
- 6.4.3 MANAGED SERVICES
7 CYBERSECURITY SOFTWARE MARKET FOR GENERATIVE AI, BY TYPE
- 7.1 INTRODUCTION
- 7.1.1 CYBERSECURITY SOFTWARE FOR GENERATIVE AI: MARKET DRIVERS
- 7.2 GENERATIVE AI TRAINING DATA SECURITY SOFTWARE
- 7.2.1 ENSURING RELIABILITY AND COMPLIANCE WITH TRAINING DATA SECURITY
- 7.2.2 DATA INTEGRITY VERIFICATION
- 7.2.3 SECURE DATA AUGMENTATION
- 7.2.4 AUTOMATED DATA CLEANING
- 7.2.5 DATA QUALITY MONITORING
- 7.2.6 DATA ANONYMIZATION
- 7.3 GENERATIVE AI MODEL SECURITY SOFTWARE
- 7.3.1 SHIELDING GENERATIVE AI MODELS AGAINST EVOLVING THREATS
- 7.3.2 MODEL INTEGRITY
- 7.3.3 ADVERSARIAL TRAINING & TESTING
- 7.3.4 SECURE MODEL TRAINING ENVIRONMENTS
- 7.3.5 MODEL DRIFT & BIAS DETECTION
- 7.3.6 ROBUSTNESS TESTING
- 7.4 GENERATIVE AI INFRASTRUCTURE SECURITY SOFTWARE
- 7.4.1 ENSURING RESILIENT FOUNDATIONS FOR LARGE-SCALE GENERATIVE AI OPERATIONS
- 7.4.2 CONTINUOUS MONITORING
- 7.4.3 AUTOMATED SECURITY PATCHING
- 7.4.4 SECURE API MANAGEMENT
- 7.4.5 REAL-TIME THREAT DETECTION
- 7.4.6 SECURITY AUDITS
- 7.5 GENERATIVE AI APPLICATION SECURITY SOFTWARE
- 7.5.1 DEFENDING GENERATIVE AI APPLICATIONS FROM ATTACK VECTORS
- 7.5.2 PROMPT INJECTION SECURITY
- 7.5.3 DATA LEAKAGE PREVENTION
- 7.5.4 USER AUTHENTICATION & ACCESS CONTROL
- 7.5.5 MONITORING & ANOMALY DETECTION
- 7.5.6 ETHICAL AI GOVERNANCE
8 GENERATIVE AI CYBERSECURITY MARKET, BY END USER
- 8.1 INTRODUCTION
- 8.1.1 END USERS: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 8.2 END USERS: GENERATIVE AI-BASED CYBERSECURITY
- 8.2.1 DRIVING ADVANCED THREAT MITIGATION WITH GENERATIVE AI
- 8.2.2 GOVERNMENT & DEFENSE
- 8.2.3 BFSI
- 8.2.4 IT & ITES
- 8.2.5 HEALTHCARE & LIFE SCIENCES
- 8.2.6 RETAIL & ECOMMERCE
- 8.2.7 MANUFACTURING
- 8.2.8 ENERGY & UTILITIES
- 8.2.9 TELECOMMUNICATIONS
- 8.2.10 AUTOMOTIVE, TRANSPORTATION, AND LOGISTICS
- 8.2.11 MEDIA & ENTERTAINMENT
- 8.2.12 OTHER END USERS
- 8.3 END USERS: CYBERSECURITY FOR GENERATIVE AI
- 8.3.1 PROTECTING GENERATIVE AI SERVICES TO SAFEGUARD END USERS
- 8.3.2 CLOUD HYPERSCALERS
- 8.3.3 MANAGED SECURITY SERVICE PROVIDERS
- 8.3.4 GENERATIVE AI PROVIDERS
- 8.3.4.1 Foundation model/LLM developers
- 8.3.4.2 Data annotators
- 8.3.4.3 Content creation platform providers
- 8.3.4.4 Generative AI-as-a-service provider
9 GENERATIVE AI-BASED CYBERSECURITY SOFTWARE MARKET, BY TYPE
- 9.1 INTRODUCTION
- 9.1.1 GENERATIVE AI-BASED CYBERSECURITY SOFTWARE MARKET DRIVERS
- 9.2 THREAT DETECTION & INTELLIGENCE SOFTWARE
- 9.2.1 OFFERS ENHANCED CYBERSECURITY PRECISION AND SPEED
- 9.2.2 AUTOMATED THREAT ANALYSIS
- 9.2.3 SECURITY INFORMATION & EVENT MANAGEMENT
- 9.2.4 AI-NATIVE SECURITY ANALYSIS
- 9.2.5 THREAT CORRELATION
- 9.2.6 THREAT INTELLIGENCE
- 9.3 RISK ASSESSMENT SOFTWARE
- 9.3.1 PREDICTIVE RISK ASSESSMENT STRENGTHENS GENERATIVE AI CYBERSECURITY POSTURE
- 9.3.2 AUTOMATED RISK INSIGHTS
- 9.3.3 IMPACT ANALYSIS
- 9.3.4 RISK INTELLIGENCE
- 9.3.5 COMPLIANCE AUTOMATION
- 9.3.6 OTHER RISK ASSESSMENT SOFTWARE
- 9.4 EXPOSURE MANAGEMENT SOFTWARE
- 9.4.1 OFFERS AI-POWERED VULNERABILITY OVERSIGHT FOR STRONGER CYBERSECURITY
- 9.4.2 VULNERABILITY ANALYSIS
- 9.4.3 EXPOSURE PRIORITIZATION
- 9.4.4 AUTOMATED EXPOSURE DETECTION
- 9.4.5 INCIDENT RESPONSE
- 9.4.6 OTHER EXPOSURE MANAGEMENT SOFTWARE
- 9.5 PHISHING SIMULATION & PREVENTION SOFTWARE
- 9.5.1 SIMULATES REALISTIC PHISHING SCENARIOS WITH GENERATIVE AI
- 9.5.2 PHISHING SIMULATION CAMPAIGNS
- 9.5.3 PHISHING ATTACK ANALYSIS
- 9.5.4 DEEPFAKE DETECTION
- 9.5.5 FRAUD PREVENTION
- 9.5.6 SOCIAL ENGINEERING DETECTION
- 9.6 REMEDIATION GUIDANCE SOFTWARE
- 9.6.1 ENABLES QUICK AND INFORMED RESPONSE WITH GENERATIVE AI REMEDIATION GUIDANCE
- 9.6.2 AUTOMATED REMEDIATION
- 9.6.3 INTERACTIVE REMEDIATION SUPPORT
- 9.6.4 PROACTIVE THREAT MANAGEMENT
- 9.6.5 COMPLIANCE REMEDIATION
- 9.6.6 OTHER REMEDIATION GUIDANCE SOFTWARE
- 9.7 THREAT HUNTING PLATFORMS
- 9.7.1 CYBER DEFENSE ENHANCED BY PREDICTING AND NEUTRALIZING STEALTH ATTACKS
- 9.7.2 REAL-TIME THREAT ANALYSIS
- 9.7.3 NATURAL LANGUAGE QUERY INTERFACE
- 9.7.4 BEHAVIOR ANALYSIS
- 9.7.5 RESPONSE AUTOMATION
- 9.7.6 OTHER THREAT HUNTING PLATFORMS
- 9.8 CODE ANALYSIS SOFTWARE
- 9.8.1 SECURES DEVELOPMENT PIPELINES WITH GENERATIVE AI PRECISION
- 9.8.2 CODE SNIPPET ANALYSIS
- 9.8.3 SOURCE CODE PROTECTION
- 9.8.4 VULNERABILITY DETECTION
- 9.8.5 AUTOMATED CODE REVIEW
- 9.8.6 COMPLIANCE CHECKS
10 GENERATIVE AI CYBERSECURITY MARKET, BY SECURITY TYPE
- 10.1 INTRODUCTION
- 10.1.1 SECURITY TYPE: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 10.2 DATABASE SECURITY
- 10.2.1 SECURES GENERATIVE AI PIPELINES WITH ADVANCED DATABASE PROTECTION
- 10.2.2 DATA LOSS PREVENTION
- 10.2.3 DATA USAGE MONITORING
- 10.2.4 DATA COMPLIANCE & GOVERNANCE
- 10.2.5 DATA ENCRYPTION
- 10.2.6 DATA MASKING & TOKENIZATION
- 10.2.7 ACCESS CONTROL
- 10.3 NETWORK SECURITY
- 10.3.1 OPTIMIZING SECURE CONNECTIVITY FOR GENERATIVE AI WORKLOADS
- 10.3.2 NETWORK TRAFFIC ANALYSIS
- 10.3.3 SECURE ACCESS SERVICE EDGE
- 10.3.4 ZERO TRUST NETWORK ACCESS
- 10.3.5 FIREWALLS
- 10.3.6 INTRUSION DETECTION/PREVENTION SYSTEMS
- 10.3.7 VPNS & SECURE TUNNELING
- 10.4 ENDPOINT SECURITY
- 10.4.1 OPTIMIZING THREAT DETECTION AND RESPONSE ACROSS GENERATIVE AI ENDPOINTS
- 10.4.2 ENDPOINT DETECTION & RESPONSE
- 10.4.3 ENDPOINT PROTECTION PLATFORMS
- 10.5 APPLICATION SECURITY
- 10.5.1 SECURING GENERATIVE AI WORKFLOWS WITH END-TO-END APPLICATION PROTECTION
- 10.5.2 STATIC APPLICATION SECURITY TESTING
- 10.5.3 DYNAMIC APPLICATION SECURITY TESTING
- 10.5.4 LLM SECURITY
- 10.5.5 RUNTIME PROTECTION
- 10.5.6 INCIDENT RESPONSE & RECOVERY
- 10.5.7 GOVERNANCE, RISK, AND COMPLIANCE
11 GENERATIVE AI CYBERSECURITY MARKET, BY REGION
- 11.1 INTRODUCTION
- 11.2 NORTH AMERICA
- 11.2.1 NORTH AMERICA: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 11.2.2 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 11.2.3 US
- 11.2.3.1 Market driven by robust technological infrastructure and culture of innovation
- 11.2.4 CANADA
- 11.2.4.1 Recent advancements and presence of leading companies to drive market
- 11.3 EUROPE
- 11.3.1 EUROPE: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 11.3.2 EUROPE: MACROECONOMIC OUTLOOK
- 11.3.3 UK
- 11.3.3.1 Commitment to leveraging AI to tackle evolving cyber threats to fuel growth
- 11.3.4 GERMANY
- 11.3.4.1 Active government promotion of AI research to boost market
- 11.3.5 FRANCE
- 11.3.5.1 Emphasis on R&D to drive market
- 11.3.6 REST OF EUROPE
- 11.4 ASIA PACIFIC
- 11.4.1 ASIA PACIFIC: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 11.4.2 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 11.4.3 CHINA
- 11.4.3.1 AI-driven cybersecurity solutions that offer robust defense against digital threats - key market driver
- 11.4.4 INDIA
- 11.4.4.1 Market trajectory characterized by significant investment in research and development
- 11.4.5 JAPAN
- 11.4.5.1 International regulatory framework and promotion of safe and trustworthy AI usage - key drivers
- 11.4.6 REST OF ASIA PACIFIC
- 11.5 MIDDLE EAST & AFRICA
- 11.5.1 MIDDLE EAST & AFRICA: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 11.5.2 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 11.5.3 SAUDI ARABIA
- 11.5.3.1 Evolving to support growth of generative AI and cybersecurity
- 11.5.4 UAE
- 11.5.4.1 Focus on establishment of cutting-edge AI and cybersecurity infrastructure
- 11.5.5 REST OF MIDDLE EAST
- 11.5.6 AFRICA
- 11.5.6.1 Development of new AI models and technologies tailored to unique cybersecurity challenges to drive market
- 11.6 LATIN AMERICA
- 11.6.1 LATIN AMERICA: GENERATIVE AI CYBERSECURITY MARKET DRIVERS
- 11.6.2 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 11.6.3 BRAZIL
- 11.6.3.1 Companies continue to invest in generative AI solutions and push boundaries of innovation
- 11.6.4 MEXICO
- 11.6.4.1 Government proactively addressing data privacy and security concerns
- 11.6.5 REST OF LATIN AMERICA
12 COMPETITIVE LANDSCAPE
- 12.1 OVERVIEW
- 12.2 KEY PLAYER STRATEGIES
- 12.3 REVENUE ANALYSIS
- 12.4 MARKET SHARE ANALYSIS
- 12.4.1 MARKET RANKING ANALYSIS
- 12.5 PRODUCT COMPARATIVE ANALYSIS
- 12.5.1 PRODUCT COMPARATIVE ANALYSIS: GENERATIVE AI-BASED CYBERSECURITY
- 12.5.1.1 Purple AI (SentinelOne)
- 12.5.1.2 Prevent (Darktrace)
- 12.5.1.3 ZDX Copilot (Zscaler)
- 12.5.1.4 FortiAI (Fortinet)
- 12.5.1.5 Precision AI (Palo Alto)
- 12.5.2 PRODUCT COMPARATIVE ANALYSIS: CYBERSECURITY FOR GENERATIVE AI
- 12.5.2.1 QRadar (IBM)
- 12.5.2.2 AI Runtime Security (Palo Alto)
- 12.5.2.3 Nitro Enclaves (AWS)
- 12.5.2.4 Zero Trust Exchange (Zscaler)
- 12.5.2.5 Nemo LLM Guardrails (NVIDIA)
- 12.5.1 PRODUCT COMPARATIVE ANALYSIS: GENERATIVE AI-BASED CYBERSECURITY
- 12.6 COMPANY VALUATION AND FINANCIAL METRICS
- 12.7 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 12.7.1 KEY PLAYERS OFFERING GENERATIVE AI-BASED CYBERSECURITY
- 12.7.2 STARS
- 12.7.3 EMERGING LEADERS
- 12.7.4 PERVASIVE PLAYERS
- 12.7.5 PARTICIPANTS
- 12.7.6 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 12.7.6.1 Company Footprint
- 12.7.6.2 Region Footprint
- 12.7.6.3 Offering footprint
- 12.7.6.4 Security type footprint
- 12.7.6.5 End user footprint
- 12.7.7 KEY PLAYERS OFFERING CYBERSECURITY SOLUTIONS FOR GENERATIVE AI
- 12.7.8 STARS
- 12.7.9 EMERGING LEADERS
- 12.7.10 PERVASIVE PLAYERS
- 12.7.11 PARTICIPANTS
- 12.7.12 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 12.7.12.1 Company Footprint
- 12.7.12.2 Regional footprint
- 12.7.12.3 Offering footprint
- 12.7.12.4 Security type footprint
- 12.7.12.5 End user footprint
- 12.8 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 12.8.1 STARTUPS/SMES OFFERING GENERATIVE AI-BASED CYBERSECURITY
- 12.8.1.1 Progressive companies
- 12.8.1.2 Responsive companies
- 12.8.1.3 Dynamic companies
- 12.8.1.4 Starting blocks
- 12.8.2 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 12.8.2.1 Detailed List of Key Startups/SMEs
- 12.8.2.2 Competitive Benchmarking of Key Startups/SMEs
- 12.8.3 STARTUPS/SMES OFFERING CYBERSECURITY SOLUTIONS FOR GENERATIVE AI
- 12.8.3.1 Progressive companies
- 12.8.3.2 Responsive companies
- 12.8.3.3 Dynamic companies
- 12.8.3.4 Starting blocks
- 12.8.4 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 12.8.4.1 Detailed List of Key Startups/SMEs
- 12.8.4.2 Competitive Benchmarking of Key Startups/SMEs
- 12.8.1 STARTUPS/SMES OFFERING GENERATIVE AI-BASED CYBERSECURITY
- 12.9 COMPETITIVE SCENARIO AND TRENDS
- 12.9.1 PRODUCT LAUNCHES AND ENHANCEMENTS
- 12.9.2 DEALS
13 COMPANY PROFILES
- 13.1 INTRODUCTION
- 13.2 GENERATIVE AI-BASED CYBERSECURITY SOLUTION PROVIDERS
- 13.2.1 MICROSOFT
- 13.2.1.1 Business overview
- 13.2.1.2 Products/Solutions/Services offered
- 13.2.1.3 Recent developments
- 13.2.1.3.1 Product launches and enhancements
- 13.2.1.3.2 Deals
- 13.2.1.4 MnM view
- 13.2.1.4.1 Right to win
- 13.2.1.4.2 Strategic choices
- 13.2.1.4.3 Weaknesses and competitive threats
- 13.2.2 IBM
- 13.2.2.1 Business overview
- 13.2.2.2 Products/Solutions/Services offered
- 13.2.2.3 Recent developments
- 13.2.2.3.1 Product launches and enhancements
- 13.2.2.3.2 Deals
- 13.2.2.4 MnM view
- 13.2.2.4.1 Right to win
- 13.2.2.4.2 Strategic choices
- 13.2.2.4.3 Weaknesses and competitive threats
- 13.2.3 GOOGLE
- 13.2.3.1 Business overview
- 13.2.3.2 Products/Solutions/Services offered
- 13.2.3.3 Recent developments
- 13.2.3.3.1 Product launches and enhancements
- 13.2.3.3.2 Deals
- 13.2.3.4 MnM view
- 13.2.3.4.1 Right to win
- 13.2.3.4.2 Strategic choices
- 13.2.3.4.3 Weaknesses and competitive threats
- 13.2.4 SENTINELONE
- 13.2.4.1 Business overview
- 13.2.4.2 Products/Solutions/Services offered
- 13.2.4.3 Recent developments
- 13.2.4.3.1 Product launches and enhancements
- 13.2.4.3.2 Deals
- 13.2.4.4 MnM view
- 13.2.4.4.1 Right to win
- 13.2.4.4.2 Strategic choices
- 13.2.4.4.3 Weaknesses and competitive threats
- 13.2.5 NVIDIA
- 13.2.5.1 Business overview
- 13.2.5.2 Products/Solutions/Services offered
- 13.2.5.3 Recent developments
- 13.2.5.3.1 Product launches and enhancements
- 13.2.5.3.2 Deals
- 13.2.6 NEURALTRUST
- 13.2.6.1 Business overview
- 13.2.6.2 Products/Solutions/Services offered
- 13.2.7 TREND MICRO
- 13.2.8 BLACKBERRY
- 13.2.9 OKTA
- 13.2.10 SANGFOR TECHNOLOGIES
- 13.2.11 VERACODE
- 13.2.12 LEXISNEXIS
- 13.2.13 SECURITYSCORECARD
- 13.2.14 BROADCOM
- 13.2.15 COHESITY
- 13.2.16 ELASTIC NV
- 13.2.17 CYBEREASON
- 13.2.18 FLASHPOINT
- 13.2.19 MOSTLY AI
- 13.2.20 RECORDED FUTURE
- 13.2.21 SECUREFRAME
- 13.2.22 SLASHNEXT
- 13.2.23 VIRUSTOTAL
- 13.2.24 XENONSTACK
- 13.2.25 ZEROFOX
- 13.2.1 MICROSOFT
- 13.3 PROVIDERS OF CYBERSECURITY SOLUTIONS FOR GENERATIVE AI
- 13.3.1 AWS
- 13.3.1.1 Business overview
- 13.3.1.2 Products/Solutions/Services offered
- 13.3.1.3 Recent developments
- 13.3.1.3.1 Deals
- 13.3.1.4 MnM view
- 13.3.1.4.1 Right to win
- 13.3.1.4.2 Strategic choices
- 13.3.1.4.3 Weaknesses and competitive threats
- 13.3.2 CISCO
- 13.3.2.1 Business overview
- 13.3.2.2 Products/Solutions/Services offered
- 13.3.2.3 Recent developments
- 13.3.2.3.1 Product launches and enhancements
- 13.3.2.3.2 Deals
- 13.3.3 CROWDSTRIKE
- 13.3.3.1 Business overview
- 13.3.3.2 Products/Solutions/Services offered
- 13.3.3.3 Recent developments
- 13.3.3.3.1 Product launches and enhancements
- 13.3.3.3.2 Deals
- 13.3.4 FORTINET
- 13.3.4.1 Business overview
- 13.3.4.2 Products/Products/Solutions/Services offered
- 13.3.4.3 Recent developments
- 13.3.4.3.1 Product launches and enhancements
- 13.3.4.3.2 Deals
- 13.3.5 ZSCALER
- 13.3.5.1 Business overview
- 13.3.5.2 Products/Solutions/Services offered
- 13.3.5.3 Recent developments
- 13.3.5.3.1 Product launches and enhancements
- 13.3.5.3.2 Deals
- 13.3.6 PALO ALTO NETWORKS
- 13.3.7 DARKTRACE
- 13.3.8 F5
- 13.3.9 SOPHOS
- 13.3.10 TRELLIX
- 13.3.11 TENABLE
- 13.3.12 SNYK
- 13.3.13 ABNORMAL SECURITY
- 13.3.14 ADVERSA AI
- 13.3.15 AQUA SECURITY
- 13.3.16 BIGID
- 13.3.17 CHECKMARX
- 13.3.18 CREDO AI
- 13.3.19 DEEPKEEP
- 13.3.20 LAKERA
- 13.3.21 SKYFLOW
- 13.3.22 TROJAI
- 13.3.1 AWS
14 ADJACENT AND RELATED MARKETS
- 14.1 INTRODUCTION
- 14.2 GENERATIVE AI MARKET - GLOBAL FORECAST TO 2032
- 14.2.1 MARKET DEFINITION
- 14.2.2 MARKET OVERVIEW
- 14.2.2.1 Generative AI market, by offering
- 14.2.2.2 Generative AI market, by data modality
- 14.2.2.3 Generative AI market, by application
- 14.2.2.4 Generative AI market, by end user
- 14.2.2.5 Generative AI market, by region
- 14.3 ARTIFICIAL INTELLIGENCE IN CYBERSECURITY MARKET - GLOBAL FORECAST TO 2028
- 14.3.1 MARKET DEFINITION
- 14.3.2 MARKET OVERVIEW
- 14.3.2.1 Artificial intelligence in cybersecurity market, by offering
- 14.3.2.2 Artificial intelligence in cybersecurity market, by security type
- 14.3.2.3 Artificial intelligence in cybersecurity market, by technology
- 14.3.2.4 Artificial intelligence in cybersecurity market, by application
- 14.3.2.5 Artificial intelligence in cybersecurity market, by vertical
- 14.3.2.6 Artificial intelligence in cybersecurity market, by region
15 APPENDIX
- 15.1 DISCUSSION GUIDE
- 15.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 15.3 CUSTOMIZATION OPTIONS
- 15.4 RELATED REPORTS
- 15.5 AUTHOR DETAILS



















