
|
시장보고서
상품코드
1812625
중요 인프라 보호 시장 : 물리적 보안, IT 사이버 보안 솔루션, OT 사이버 보안 - 예측(-2030년)Critical Infrastructure Protection Market by Physical Security (Perimeter Protection, Screening & Scanning Systems), IT Cybersecurity Solutions (Compliance & Policy Management, IAM), and OT Cybersecurity (Digital Twin Platform) - Global Forecast to 2030 |
||||||
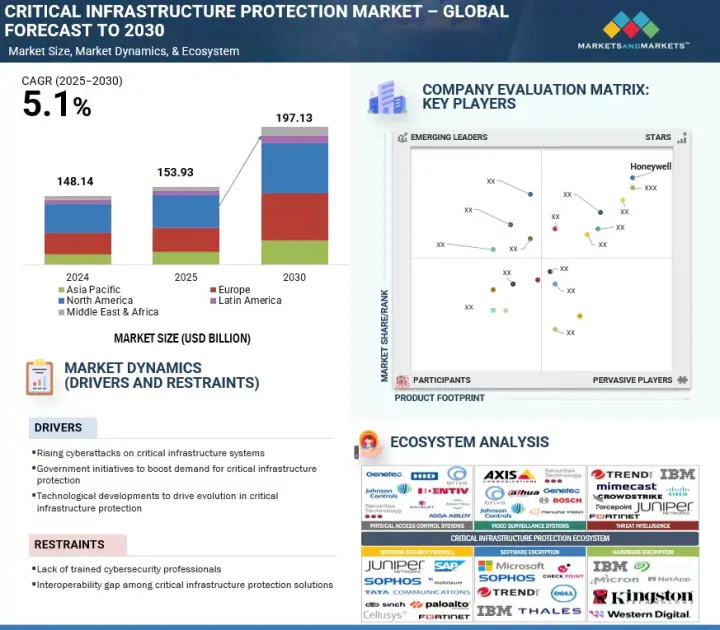
세계의 중요 인프라 보호(CIP) 시장 규모는 2025년 1,539억 3,000만 달러에서 2030년까지 1,971억 3,000만 달러에 달할 것으로 예측되며, 예측 기간에 CAGR로 5.1%의 성장이 전망됩니다.
진화하는 사이버 위협과 물리적 위협으로부터 중요한 자산과 서비스를 보호하려는 수요가 증가하면서 시장을 주도하고 있습니다.
| 조사 범위 | |
|---|---|
| 조사 대상 연도 | 2019-2030년 |
| 기준 연도 | 2024년 |
| 예측 기간 | 2025-2030년 |
| 단위 | 100만 달러/10억 달러 |
| 부문 | 제공, 업계, 지역 |
| 대상 지역 | 북미, 유럽, 아시아태평양, 중동 및 아프리카, 라틴아메리카 |
조직은 고급 모니터링, 액세스 제어, 위협 탐지 및 사이버 보안 조치를 결합한 통합 보호 솔루션을 광범위하게 채택하여 복원력을 강화하고 있습니다. 이를 통해 에너지, 유틸리티, 운송 부문에서 다운타임 감소, 리스크 감소, 업무 연속성을 보장하고 있습니다.
그러나 CIP 솔루션 간의 상호운용성 격차가 큰 걸림돌로 작용하고 있습니다. 많은 도구가 사일로 내에서 개발되어 효과적으로 통합할 수 없는 단편적인 보호가 이루어지고 있습니다. 이로 인해 보안 관리가 복잡해지고, 중요한 자산이 취약한 상태로 방치되고 있습니다. 또한, 민관 협력과 정보 공유가 제한적이기 때문에 통일된 방어 전략을 수립하는 데 어려움을 겪고 있습니다.
"물리적 보안 제공 중 서비스 부문이 예측 기간 동안 가장 높은 CAGR을 기록할 것으로 예상됩니다."
이러한 성장의 원동력은 중요 시설을 안전하게 보호하기 위한 설계, 컨설팅, 통합, 유지보수, 관리 서비스에 대한 수요 증가에 기인합니다. 조직이 진화하는 위협에 직면하면서 첨단 물리 보안 시스템 구축과 지속적인 모니터링 및 지원을 보장하기 위해 전문 서비스 제공업체에 대한 의존도가 크게 증가하고 있습니다. 이러한 추세는 전문 지식과 지속적인 서비스 제공이 중요 인프라의 복원력을 강화하는 데 있어 중요한 역할을 하고 있음을 보여줍니다.
"OT 및 ICS 보안 플랫폼 부문이 예측 기간 동안 가장 큰 시장 점유율을 차지할 것으로 예상됩니다."
OT 사이버 보안 솔루션별로는 OT 및 ICS 보안 플랫폼 부문이 예측 기간 동안 가장 큰 시장 점유율을 차지할 것으로 예상됩니다. 이러한 우위는 산업용 제어 시스템(ICS), SCADA 시스템, 기타 미션 크리티컬한 인프라를 포함한 운영 기술 환경을 보호해야 할 필요성이 높아졌기 때문입니다. 산업 네트워크를 겨냥한 사이버 공격의 빈도가 증가하고, IT 시스템과 OT 시스템의 융합이 진행됨에 따라 기업들은 종합적인 OT-ICS 보안 플랫폼을 우선시하고 있습니다. 이 솔루션은 자산 가시성, 실시간 위협 탐지, 지능형 지속적 위협으로부터 보호하고, 에너지, 유틸리티, 석유 및 가스, 제조와 같은 중요한 부문에서 운영의 복원력을 보장하고 다운타임을 최소화합니다.
"북미가 예측 기간 동안 가장 큰 시장 점유율을 차지할 것으로 예상됩니다."
북미는 전체 지역 중 가장 큰 시장 점유율을 차지하고 있습니다. 또한, 강력한 규제 프레임워크, 보안 기술에 대한 높은 투자, 통합 보호 솔루션의 조기 도입으로 CIP 시장을 선도하고 있습니다. 에너지, 금융, 운송이 주요 타겟인 북미에서는 첨단 CIP 시스템의 대규모 구축에 중점을 두고 있습니다. 또한, 정부의 노력, 사이버 보안 의무화, 부서 간 협력은 미국과 캐나다의 채택을 더욱 가속화하고 있습니다.
세계의 중요 인프라 보호 시장에 대해 조사 분석했으며, 주요 촉진요인과 저해요인, 경쟁 상황, 향후 동향 등의 정보를 전해드립니다.
목차
제1장 소개
제2장 조사 방법
제3장 주요 요약
제4장 중요한 인사이트
- 주요 시장 기업에서 매력적인 기회
- 중요 인프라 보호 시장 : 제공별
- 중요 인프라 보호 시장 : 물리적 보안 제공별
- 중요 인프라 보호 시장 : 시스템별
- 중요 인프라 보호 시장 : 서비스별
- 중요 인프라 보호 시장 : IT 사이버 보안 제공별
- 중요 인프라 보호 시장, IT 사이버 보안 솔루션별
- 중요 인프라 보호 시장, IT 사이버 보안 서비스별
- 중요 인프라 보호 시장 : OT 사이버 보안 제공별
- 중요 인프라 보호 시장 : OT 사이버 보안 솔루션별
- 중요 인프라 보호 시장 : OT 사이버 보안 서비스별
- 중요 인프라 보호 시장 : 업계별
- 시장 투자 시나리오
제5장 시장 개요와 산업 동향
- 소개
- 시장 역학
- 성장 촉진요인
- 성장 억제요인
- 기회
- 과제
- 사례 연구 분석
- 사례 연구 1 : ALTA, 제로 트러스트 CDR로 악성 파일 업로드 방지
- 사례 연구 2 : 이탈리아 장비 제조사, ForcePoint로 내부 위협 방어
- 사례 연구 3 : AXIS 360도 카메라와 DEDRONE의 드론 대응 솔루션으로 CONSOLIDATED EDISON의 순찰 공역 관리
- 사례 연구 4 : TOSIBOX, NWCPUD 유틸리티의 원격 연결성 혁신
- 사례 연구 5 : 마니팔 대학교, HONEYWELL의 스마트 카드 솔루션으로 물리적 보안 및 캠퍼스 운영 강화
- 사례 연구 6 : ADT 통합 감시 시스템으로 더블린 공항 터미널 2의 물리적 보안 및 운영 효율성 향상
- 사례 연구 7 : WESCO 통합 네트워크 업그레이드로 지방자치단체 하수도 인프라의 물리적 보안 및 사이버 보안 강화
- 사례 연구 8 : CHESAPEAKE BAY BRIDGE-TUNNEL의 PELCO 물리적 보안 혁신으로 주요 교통로 확보
- 사례 연구 9 : 하우라키 지구 의회, 다크트레이스 AI 활용으로 중요 인프라 보호 및 제3자 위험 관리
- 사례 연구 10 : 알고섹, NCR의 제로 트러스트 보안 구현 지원
- 밸류체인 분석
- 컴포넌트 프로바이더
- 조직 계획과 설계
- 솔루션·서비스 프로바이더
- 시스템 통합사업자
- 소매/유통 채널
- 최종사용자
- 생태계 분석
- Porter's Five Forces 분석
- 주요 이해관계자와 구입 기준
- 중요 인프라 보호 시장에 대한 생성형 AI의 영향
- 생성형 AI
- 중요 인프라 보호 시장의 주요 이용 사례와 시장 전망
- 상호 접속된 인접 생태계에 대한 생성형 AI의 영향
- 가격 책정 분석
- 주요 기업 평균판매가격 동향 : 시스템별(2024년)
- 참고 가격 분석 : 제공별(2024년)
- 기술 분석
- 주요 기술
- 보완 기술
- 인접 기술
- 특허 분석
- 관세와 규제 상황
- 중요 인프라 보호 제품에 관한 관세
- 규제기관, 정부기관, 기타 조직
- 주요 규제
- 고객 비즈니스에 영향을 미치는 동향과 혼란
- 무역 분석
- 수입 데이터
- 수출 데이터
- 중요 인프라 보호 시장에 대한 미국의 트럼프 관세의 영향(2025년)
- 소개
- 주요 관세율
- 가격의 영향 분석
- 국가/지역에 대한 영향
- 주요 회의와 이벤트(2025-2026년)
- 투자와 자금 조달 시나리오
제6장 중요 인프라 보호 시장 : 제공별
- 소개
- 물리적 보안 제공
- IT 사이버 보안 솔루션
- OT 사이버 보안 솔루션
제7장 중요 인프라 보호 시장 : 업계별
- 소개
- 금융기관
- 정부
- 방위
- 운송·물류
- 에너지·전력
- 상업 부문
- 통신
- 화학제품·제조
- 석유 및 가스
- 기타 업계
제8장 중요 인프라 보호 시장 : 지역별
- 소개
- 북미
- 북미 시장 촉진요인
- 북미의 거시경제 전망
- 미국
- 캐나다
- 아시아태평양
- 아시아태평양 시장 촉진요인
- 아시아태평양의 거시경제 전망
- 중국
- 일본
- 인도
- 기타 아시아태평양
- 유럽
- 유럽 시장 촉진요인
- 유럽의 거시경제 전망
- 영국
- 독일
- 프랑스
- 이탈리아
- 기타 유럽
- 중동 및 아프리카
- 중동 및 아프리카 시장 촉진요인
- 중동 및 아프리카의 거시경제 전망
- GCC
- 남아프리카공화국
- 기타 중동 및 아프리카
- 라틴아메리카
- 라틴아메리카 시장 촉진요인
- 라틴아메리카의 거시경제 전망
- 브라질
- 멕시코
- 기타 라틴아메리카
제9장 경쟁 구도
- 주요 진출 기업의 전략/강점(2022-2024년)
- 매출 분석(2020-2024년)
- 시장 점유율 분석(2024년)
- 브랜드/제품의 비교
- HONEYWELL
- BAE SYSTEMS
- THALES
- NORTHROP GRUMMAN
- MOTOROLA SOLUTIONS
- 기업 평가와 재무 지표
- 기업 평가 매트릭스 : 주요 기업(2024년)
- 기업 평가 매트릭스 : 스타트업/중소기업(2024년)
- 경쟁 시나리오
제10장 기업 개요
- 소개
- 주요 기업
- AXIS COMMUNICATIONS
- FORCEPOINT
- FORTINET
- CISCO
- BAE SYSTEMS
- LOCKHEED MARTIN
- GENERAL DYNAMICS
- NORTHROP GRUMMAN
- HONEYWELL
- AIRBUS
- THALES
- HEXAGON AB
- JOHNSON CONTROLS
- MOTOROLA SOLUTIONS
- TENABLE
- ROLTA
- SERVICENOW
- LUNA-OPTASENSE
- TELTRONIC
- WATERFALL SECURITY SOLUTIONS
- WESTMINISTER GROUP PLC
- OWL CYBER DEFENSE SOLUTIONS
- ACHILLES HEEL TECHNOLOGIES
- CIPS SECURITY
- SUPREMA INC
- INDUSTRIAL DEFENDER
- TERMA
- ERICSSON
- RHEBO AG
- LEIDOS
- MECOM MEDIEN-COMMUNICATIONS
- KLOCH
- SIEMENS
- CAMBIUM NETWORKS
- HUAWEI
- G4S
- GE VERNOVA
- NEC CORPORATION
- BRUKER CORPORATION
- FUJITSU
제11장 인접 시장
- 소개
- 사이버 보안 시장
- 운영 기술(OT) 보안 시장
제12장 부록
KSM 25.09.25The global CIP market size is projected to grow from USD 153.93 billion in 2025 to USD 197.13 billion by 2030 at a compound annual growth rate (CAGR) of 5.1% during the forecast period. The rising need to safeguard essential assets and services against evolving cyber and physical threats drives the market.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/USD Billion) |
| Segments | Offering, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
Organizations are widely adopting integrated protection solutions that combine advanced surveillance, access control, threat detection, and cybersecurity measures to strengthen resilience. This reduces downtime, mitigates risks, and ensures continuity of operations across the energy, utilities, and transportation sectors.

However, a major restraint is the interoperability gap among CIP solutions. Many tools are developed in silos, resulting in fragmented protection that fails to integrate effectively. This complicates security management and leaves critical assets vulnerable. Furthermore, limited coordination and information sharing between the government and private sectors hinder unified defense strategies.
"Services segment within the physical security offerings is expected to record the highest CAGR during the forecast period"
The services segment within physical security offerings is projected to witness the highest CAGR during the forecast period. This growth is driven by the increasing demand for design, consulting, integration, maintenance, and managed services to ensure robust protection of critical facilities. As organizations face evolving threats, reliance on specialized service providers for deploying advanced physical security systems and ensuring continuous monitoring and support has grown significantly. The trend highlights the crucial role of professional expertise and ongoing service delivery in enhancing the resilience of critical infrastructure.
"OT & ICS security platform segment is projected to hold the largest market share during the forecast period"
By OT cybersecurity solutions, the OT & ICS security platform segment is expected to hold the largest market share within OT cybersecurity solutions during the forecast period. This dominance is driven by the increasing need to secure operational technology environments, including industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, and other mission-critical infrastructure. With the rising frequency of cyberattacks targeting industrial networks and the growing convergence of IT and OT systems, organizations are prioritizing comprehensive OT & ICS security platforms. These solutions provide asset visibility, real-time threat detection, and protection against advanced persistent threats, ensuring operational resilience and minimizing downtime in critical sectors such as energy, utilities, oil & gas, and manufacturing.
"North America is expected to hold the largest market share during forecast period"
North America accounts for the largest market share among all regions. It leads the CIP market due to strong regulatory frameworks, high investments in security technologies, and early adoption of integrated protection solutions. With energy, finance, and transportation being prime targets, North America emphasizes large-scale deployment of advanced CIP systems. Additionally, government initiatives, cybersecurity mandates, and cross-sector collaboration further accelerate adoption across the US and Canada.
Breakdown of primaries
The study contains insights from various industry experts, from component suppliers to Tier 1 companies and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 40%, Tier 2 - 35%, and Tier 3 - 25%
- By Designation: C-level - 45%, Directors - 35%, and Managers - 20%
- By Region: North America - 55%, Europe - 25%, Asia Pacific - 15%, RoW - 5%
The key players in the CIP market include BAE Systems (US), Lockheed Martin (US), General Dynamics (US), Northrop Grumman (US), Honeywell (US), Airbus (France), Thales (France), Hexagon AB (Sweden), Johnson Controls (US), Motorola Solutions (US), Axis Communications (Sweden), Forcepoint (US), Fortinet (US), Cisco (US), Huawei (China), and others.
The study includes an in-depth competitive analysis of the key players in the CIP market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the CIP market and forecasts its size by offering into Physical Security Offering (Systems {Perimeter Protection, Surveillance & Monitoring Systems, Access Control Systems, Screening & Scanning Systems, and Emergency Communication Systems} and Services {Professional Services and Managed Services}, IT Cybersecurity Solutions (Solutions (Network & Endpoint Protection, Identity & Access Management (IAM) Solutions, Cloud & Application Security, Encryption & Data Protection, Threat Detection & Response Platform, Compliance & Policy Management, Patch Management, and Data Backup & Recovery} and Services {Professional Services and Managed Services}) and OT Cybersecurity Solutions (Solution {OT & ICS Security Platform, IoT & IIoT Security Solutions, OT Threat Detection & Monitoring, Digital Twin Platform, and Asset Identification & Visibility} and Services {Professional Services and Managed Services}). The verticals covered in the CIP market include Financial Institutions, Government, Defense, Transport & Logistics, Energy & Power, Commercial Sector, Telecom, Chemicals & Manufacturing, Oil & Gas, and Other Verticals. By region, the market is segmented into North America, Europe, Asia Pacific, Middle East & Africa, and Latin America.
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders and new entrants with information on the closest approximations of the revenue numbers for the overall CIP market and the subsegments. It will also help stakeholders understand the competitive landscape and gain more insights to better position their businesses and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
- Analysis of key drivers (rising cyberattacks on critical infrastructure systems, government initiatives to boost demand for critical infrastructure protection, and technological developments to drive evolution in critical infrastructure protection), restraints (lack of trained cybersecurity professionals and interoperability gap among critical infrastructure protection solutions), opportunities (rising adoption of IoT and rising infrastructure investment spurs demand for enhanced protection measures), and challenges (supply chain vulnerabilities threaten critical infrastructure and high implementation and maintenance cost)
- Product Development/Innovation: Detailed insights into upcoming technologies, research & development activities, and new product & service launches in the CIP market
- Market Development: Comprehensive information about lucrative markets - analysis of the CIP market across varied regions
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the CIP market
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players such as BAE Systems (US), Lockheed Martin (US), General Dynamics (US), Northrop Grumman (US), Honeywell (US), Airbus (France), Thales (France), Hexagon AB (Sweden), Johnson Controls (US), Motorola Solutions (US), Axis Communications (Sweden), Forcepoint (US), Fortinet (US), Cisco (US), Huawei (China), G4S (UK), GE Vernova (US), NEC (Japan), Bruker (US), Fujitsu (Japan), Tenable (US), Rolta (India), ServiceNow (US), Luna-OptaSense (UK), Teltronic (Spain), Waterfall Security Solutions (Israel), Westminster Group (UK), Owl Cyber Defense Solutions (US), Achilles Heel Technologies (US), CIPS Security (US), Suprema Inc. (South Korea), Industrial Defender (US), Terma (Denmark), Ericsson (Sweden), Rehbo AG (Germany), Leidos (US), Mecom Medien-Communications (Germany), Kloch (US), Siemens (Germany), and Cambium Networks (US)
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION AND REGIONAL SCOPE
- 1.3.2 INCLUSIONS AND EXCLUSIONS
- 1.3.3 YEARS CONSIDERED
- 1.4 CURRENCY CONSIDERED
- 1.5 STAKEHOLDERS
- 1.6 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Breakup of primaries
- 2.1.2.2 Key industry insights
- 2.2 MARKET BREAKUP AND DATA TRIANGULATION
- 2.3 MARKET SIZE ESTIMATION
- 2.3.1 TOP-DOWN APPROACH
- 2.3.2 BOTTOM-UP APPROACH
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR KEY MARKET PLAYERS
- 4.2 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OFFERING
- 4.3 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY PHYSICAL SECURITY OFFERING
- 4.4 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SYSTEM
- 4.5 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SERVICE
- 4.6 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY IT CYBERSECURITY OFFERING
- 4.7 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY IT CYBERSECURITY SOLUTION
- 4.8 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY IT CYBERSECURITY SERVICE
- 4.9 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OT CYBERSECURITY OFFERING
- 4.10 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OT CYBERSECURITY SOLUTION
- 4.11 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OT CYBERSECURITY SERVICE
- 4.12 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY VERTICAL
- 4.13 MARKET INVESTMENT SCENARIO
5 MARKET OVERVIEW AND INDUSTRY TRENDS
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Rising cyberattacks on critical infrastructure systems
- 5.2.1.2 Government initiatives to boost demand for critical infrastructure protection
- 5.2.1.3 Technological developments to drive evolution in critical infrastructure protection
- 5.2.2 RESTRAINTS
- 5.2.2.1 Lack of trained cybersecurity professionals
- 5.2.2.2 Interoperability gap among critical infrastructure protection solutions
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Rising adoption of IoT
- 5.2.3.2 Rising infrastructure investment to spur demand for enhanced protection measures
- 5.2.4 CHALLENGES
- 5.2.4.1 Supply chain vulnerabilities to threaten critical infrastructure
- 5.2.4.2 High implementation and maintenance costs
- 5.2.1 DRIVERS
- 5.3 CASE STUDY ANALYSIS
- 5.3.1 CASE STUDY 1: ALTA PREVENTED MALICIOUS FILE UPLOADS WITH ZERO TRUST CDR
- 5.3.2 CASE STUDY 2: ITALIAN EQUIPMENT MANUFACTURER GUARDED AGAINST INSIDER THREATS WITH FORCEPOINT
- 5.3.3 CASE STUDY 3: CONSOLIDATED EDISON-PATROLLED AIRSPACE WITH AXIS 360-DEGREE CAMERAS AND DEDRONE COUNTER-DRONE SOLUTION
- 5.3.4 CASE STUDY 4: TOSIBOX REVOLUTIONIZED REMOTE CONNECTIVITY FOR NWCPUD UTILITIES
- 5.3.5 CASE STUDY 5: MANIPAL UNIVERSITY STRENGTHENED PHYSICAL SECURITY AND CAMPUS OPERATIONS WITH HONEYWELL'S SMART CARD SOLUTION
- 5.3.6 CASE STUDY 6: ADT'S INTEGRATED SURVEILLANCE ENHANCED PHYSICAL SECURITY AND OPERATIONAL EFFICIENCY AT DUBLIN AIRPORT TERMINAL 2
- 5.3.7 CASE STUDY 7: WESCO'S INTEGRATED NETWORK UPGRADE STRENGTHENED PHYSICAL AND CYBERSECURITY IN MUNICIPAL WASTEWATER INFRASTRUCTURE
- 5.3.8 CASE STUDY 8: PELCO'S PHYSICAL SECURITY TRANSFORMATION AT CHESAPEAKE BAY BRIDGE-TUNNEL SECURED VITAL TRANSPORTATION LINK
- 5.3.9 CASE STUDY 9: HAURAKI DISTRICT COUNCIL SECURED CRITICAL INFRASTRUCTURE AND MANAGED THIRD-PARTY RISK WITH DARKTRACE AI
- 5.3.10 CASE STUDY 10: ALGOSEC HELPED NCR CORPORATION ACHIEVE ZERO TRUST SECURITY
- 5.4 VALUE CHAIN ANALYSIS
- 5.4.1 COMPONENT PROVIDERS
- 5.4.2 PLANNING AND DESIGNING ORGANIZATIONS
- 5.4.3 SOLUTION AND SERVICE PROVIDERS
- 5.4.4 SYSTEM INTEGRATORS
- 5.4.5 RETAIL/DISTRIBUTION CHANNELS
- 5.4.6 END USERS
- 5.5 ECOSYSTEM ANALYSIS
- 5.6 PORTER'S FIVE FORCES ANALYSIS
- 5.6.1 THREAT OF NEW ENTRANTS
- 5.6.2 THREAT OF SUBSTITUTES
- 5.6.3 BARGAINING POWER OF SUPPLIERS
- 5.6.4 BARGAINING POWER OF BUYERS
- 5.6.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.7 KEY STAKEHOLDERS AND BUYING CRITERIA
- 5.7.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 5.7.2 BUYING CRITERIA
- 5.8 IMPACT OF GENERATIVE AI ON CRITICAL INFRASTRUCTURE PROTECTION MARKET
- 5.8.1 GENERATIVE AI
- 5.8.2 TOP USE CASES AND MARKET POTENTIAL FOR CRITICAL INFRASTRUCTURE PROTECTION MARKET
- 5.8.3 IMPACT OF GEN AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- 5.8.3.1 OT Security
- 5.8.3.2 Physical Security
- 5.8.3.3 Cybersecurity
- 5.8.3.4 Incident Response
- 5.8.3.5 Critical Incident Reconstruction
- 5.9 PRICING ANALYSIS
- 5.9.1 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY SYSTEM, 2024
- 5.9.2 INDICATIVE PRICING ANALYSIS, BY OFFERING, 2024
- 5.10 TECHNOLOGY ANALYSIS
- 5.10.1 KEY TECHNOLOGIES
- 5.10.1.1 AI & ML for Predictive Security
- 5.10.1.2 Operational Technology (OT) Security Platforms
- 5.10.1.3 IoT
- 5.10.1.4 Quantum-resistant Cybersecurity
- 5.10.1.5 5G & Edge Computer for CIP
- 5.10.2 COMPLEMENTARY TECHNOLOGIES
- 5.10.2.1 Big Data Analytics
- 5.10.2.2 Blockchain Technology
- 5.10.3 ADJACENT TECHNOLOGIES
- 5.10.3.1 Zero Trust Architecture
- 5.10.3.2 Extended Detection and Response
- 5.10.3.3 Drones
- 5.10.3.4 Biometrics
- 5.10.1 KEY TECHNOLOGIES
- 5.11 PATENT ANALYSIS
- 5.12 TARIFF AND REGULATORY LANDSCAPE
- 5.12.1 TARIFF RELATED TO CRITICAL INFRASTRUCTURE PROTECTION PRODUCTS
- 5.12.2 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 5.12.3 KEY REGULATIONS
- 5.12.3.1 US Critical Infrastructure Information Act
- 5.12.3.2 North American Electric Reliability Corporation Critical Infrastructure Protection
- 5.12.3.3 European Program for Critical Infrastructure Protection
- 5.12.3.4 IT Security Act of Germany
- 5.12.3.5 Information Technology Act of 2002 of India
- 5.12.3.6 Cybersecurity Law of People's Republic of China
- 5.12.3.7 Cybersecurity Act of Singapore
- 5.13 TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.14 TRADE ANALYSIS
- 5.14.1 IMPORT DATA
- 5.14.2 EXPORT DATA
- 5.15 IMPACT OF 2025 US TRUMP TARIFF ON CRITICAL INFRASTRUCTURE PROTECTION MARKET
- 5.15.1 INTRODUCTION
- 5.15.2 KEY TARIFF RATES
- 5.15.3 PRICE IMPACT ANALYSIS
- 5.15.4 IMPACT ON COUNTRY/REGION
- 5.15.4.1 North America
- 5.15.4.1.1 US
- 5.15.4.1.2 Canada
- 5.15.4.1.3 Mexico
- 5.15.4.2 Europe
- 5.15.4.2.1 Germany
- 5.15.4.2.2 France
- 5.15.4.2.3 United Kingdom
- 5.15.4.3 Asia Pacific
- 5.15.4.3.1 China
- 5.15.4.3.2 India
- 5.15.4.3.3 Japan
- 5.15.4.1 North America
- 5.16 KEY CONFERENCES & EVENTS IN 2025-2026
- 5.17 INVESTMENT AND FUNDING SCENARIO
6 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OFFERING
- 6.1 INTRODUCTION
- 6.1.1 OFFERING: CRITICAL INFRASTRUCTURE PROTECTION MARKET DRIVERS
- 6.2 PHYSICAL SECURITY OFFERINGS
- 6.2.1 SYSTEMS
- 6.2.1.1 Perimeter protection
- 6.2.1.1.1 Enhancing perimeter protection to safeguard first line of defense
- 6.2.1.1.2 Intrusion detection systems
- 6.2.1.1.3 Physical barriers (gates, bollards, fencing)
- 6.2.1.2 Surveillance & monitoring systems
- 6.2.1.2.1 Enhancing situational awareness with surveillance and monitoring systems
- 6.2.1.2.2 CCTV systems (fixed and PTZ cameras)
- 6.2.1.2.3 Thermal & multi-sensor units
- 6.2.1.2.4 AI-enabled smart video analytics
- 6.2.1.2.5 Drone surveillance platforms
- 6.2.1.2.6 Counter-drone detection & neutralization
- 6.2.1.2.7 Video management software (VMS)
- 6.2.1.3 Access control systems
- 6.2.1.3.1 Strengthening identity verification to counter insider threats
- 6.2.1.3.2 Smart card access solutions
- 6.2.1.3.3 Biometric identity verification systems
- 6.2.1.3.4 Mobile device-based access control
- 6.2.1.3.5 Visitor management systems
- 6.2.1.4 Screening & scanning systems
- 6.2.1.4.1 Enhancing threat detection with multi-layered screening
- 6.2.1.4.2 X-Ray scanning solutions (baggage and cargo)
- 6.2.1.4.3 Metal detection equipment
- 6.2.1.4.4 Explosive & hazardous material detection systems
- 6.2.1.5 Emergency communication systems
- 6.2.1.5.1 Building resilient and responsive communication networks
- 6.2.1.5.2 Audible & visual alert systems
- 6.2.1.5.3 Public address & mass notification platforms
- 6.2.1.1 Perimeter protection
- 6.2.2 SERVICES (PHYSICAL SECURITY OFFERING)
- 6.2.2.1 Professional services
- 6.2.2.1.1 Securing infrastructure through professional services
- 6.2.2.1.2 Design, Consulting, & Implementation Services
- 6.2.2.1.3 Risk assessment & compliance consulting
- 6.2.2.1.4 Training & Education
- 6.2.2.1.5 Support & Maintenance
- 6.2.2.2 Managed services
- 6.2.2.2.1 Streamlining protection through managed security services
- 6.2.2.1 Professional services
- 6.2.1 SYSTEMS
- 6.3 IT CYBERSECURITY SOLUTIONS
- 6.3.1 SOLUTIONS
- 6.3.1.1 Network & endpoint protection
- 6.3.1.1.1 Defending first line with network & endpoint protection
- 6.3.1.1.2 Firewalls & NAC
- 6.3.1.1.3 EPP & XDR platforms
- 6.3.1.1.4 VPN & Zero Trust Network Access
- 6.3.1.1.5 Antivirus/Antimalware Solutions
- 6.3.1.2 Identity & access management solutions
- 6.3.1.2.1 Enforcing digital trust with IAM solutions for robust authentication mechanisms
- 6.3.1.3 Cloud & application security
- 6.3.1.3.1 Protecting digital transformation by rapid adoption of cloud computing, SaaS applications, and DevOps-driven innovation
- 6.3.1.4 Encryption & data protection
- 6.3.1.4.1 Safeguarding information assets to ensure confidentiality
- 6.3.1.5 Threat detection & response platforms
- 6.3.1.5.1 Intelligent defense with rapid detection and response to address modern, sophisticated attacks that bypass traditional defenses
- 6.3.1.5.2 Log Management & SIEM
- 6.3.1.5.3 Security Orchestration, Automation, and Response (SOAR)
- 6.3.1.6 Compliance & policy management
- 6.3.1.6.1 Aligning regulations with compliance & policy management solutions
- 6.3.1.7 Patch management
- 6.3.1.7.1 Intelligent defense with rapid detection and response to address vulnerabilities in operating systems
- 6.3.1.7.2 Automated Patch Deployment Tools
- 6.3.1.7.3 Vulnerability Assessment & Remediation
- 6.3.1.8 Data backup & recovery
- 6.3.1.8.1 Ensuring business continuity with data backup & recovery solutions
- 6.3.1.8.2 Disaster Recovery-as-a-Service (DRaaS)
- 6.3.1.8.3 Backup Automation & Orchestration Tools
- 6.3.1.1 Network & endpoint protection
- 6.3.2 SERVICES
- 6.3.2.1 Professional services
- 6.3.2.1.1 Guiding cybersecurity transformation through professional services
- 6.3.2.1.2 Design, Consulting, & Implementation Services
- 6.3.2.1.3 Risk & Threat Management
- 6.3.2.1.4 Training & Education
- 6.3.2.1.5 Support & Maintenance
- 6.3.2.2 Managed services
- 6.3.2.2.1 Outsourcing security operations for cybersecurity management
- 6.3.2.1 Professional services
- 6.3.1 SOLUTIONS
- 6.4 OT CYBERSECURITY SOLUTIONS
- 6.4.1 SOLUTIONS
- 6.4.1.1 OT & ICS security platform
- 6.4.1.1.1 Safeguarding industrial control systems against external cyberattacks and insider threats
- 6.4.1.1.2 SCADA Network Security Systems
- 6.4.1.1.3 Industrial Control System (ICS) security solutions
- 6.4.1.1.4 Firewall solutions
- 6.4.1.2 IoT & IIoT Security Solutions
- 6.4.1.2.1 Safeguarding connected operational environments by detecting malicious patterns
- 6.4.1.2.2 Secure device authentication & management
- 6.4.1.2.3 Network segmentation
- 6.4.1.2.4 Anomaly detection
- 6.4.1.1 OT & ICS security platform
- 6.4.2 OT THREAT DETECTION & MONITORING
- 6.4.2.1 Staying alert against external cyberattacks and insider threats
- 6.4.2.1.1 SIEM solutions
- 6.4.2.1.2 Behavioral anomaly detection
- 6.4.2.1 Staying alert against external cyberattacks and insider threats
- 6.4.3 DIGITAL TWIN PLATFORMS
- 6.4.3.1 Building cyber-resilient models to simulate and predict cyber risks
- 6.4.3.1.1 Predictive analysis
- 6.4.3.1.2 Security scenario simulation and response planning
- 6.4.3.1 Building cyber-resilient models to simulate and predict cyber risks
- 6.4.4 ASSET IDENTIFICATION & VISIBILITY
- 6.4.4.1 Uncovering hidden risks in OT networks
- 6.4.4.1.1 Asset discovery tools
- 6.4.4.1.2 Configuration management databases services
- 6.4.4.1 Uncovering hidden risks in OT networks
- 6.4.5 SERVICES
- 6.4.5.1 Professional services
- 6.4.5.1.1 Expert guidance for industrial security to address OT cybersecurity challenges
- 6.4.5.1.2 OT cybersecurity compliance & risk advisory
- 6.4.5.1.3 Design & integration services
- 6.4.5.1.4 Industrial incident preparedness training
- 6.4.5.2 Managed services
- 6.4.5.2.1 Continuous protection for critical operations
- 6.4.5.1 Professional services
- 6.4.1 SOLUTIONS
7 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY VERTICAL
- 7.1 INTRODUCTION
- 7.1.1 VERTICAL: CRITICAL INFRASTRUCTURE PROTECTION MARKET DRIVERS
- 7.2 FINANCIAL INSTITUTIONS
- 7.2.1 FINANCIAL INSTITUTIONS TO ENSURE ADHERENCE TO STRICT REGULATIONS BY ADOPTING CIP
- 7.3 GOVERNMENT
- 7.3.1 GROWTH IN CYBER THREATS FACED BY GOVERNMENT AGENCIES TO DRIVE ADOPTION OF CIP
- 7.4 DEFENSE
- 7.4.1 CYBERSECURITY COLLABORATION TO STRENGTHEN DEFENSE INFRASTRUCTURE
- 7.5 TRANSPORT & LOGISTICS
- 7.5.1 ENHANCED SECURITY MEASURES TO SAFEGUARD TRANSPORTATION NETWORKS
- 7.5.2 HIGHWAYS & BRIDGES
- 7.5.3 RAILWAY INFRASTRUCTURE
- 7.5.4 SEAPORTS
- 7.5.5 AIRPORTS
- 7.6 ENERGY & POWER
- 7.6.1 EFFICIENCY OF PRODUCTION PROCESSES IN HIGH-RISK ENVIRONMENTS TO DRIVE MARKET
- 7.6.2 THERMAL POWER PLANTS
- 7.6.3 NUCLEAR POWER PLANTS
- 7.6.4 RENEWABLE ENERGY POWER PLANTS
- 7.7 COMMERCIAL SECTOR
- 7.7.1 NEED FOR ADVANCED AI DEFENSES TO COMBAT INCREASING INCIDENCES OF CYBERTHREATS
- 7.8 TELECOM
- 7.8.1 NECESSITY FOR SAFEGUARDING IT AND TELECOMMUNICATION NETWORKS FROM HACKERS
- 7.9 CHEMICALS & MANUFACTURING
- 7.9.1 IMPORTANCE OF KEEN SURVEILLANCE FOR SAFETY IN HAZARDOUS ENVIRONMENTS
- 7.10 OIL & GAS
- 7.10.1 POLITICAL TURMOIL IN OIL-RICH COUNTRIES TO INCREASE RISK OF CYBER-ATTACKS
- 7.10.2 UPSTREAM
- 7.10.3 DOWNSTREAM
- 7.10.4 MIDSTREAM
- 7.11 OTHER VERTICALS
- 7.11.1 WATER & WASTEWATER SECTOR
8 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY REGION
- 8.1 INTRODUCTION
- 8.2 NORTH AMERICA
- 8.2.1 NORTH AMERICA: MARKET DRIVERS
- 8.2.2 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 8.2.3 US
- 8.2.3.1 Government initiatives to strengthen critical infrastructure cybersecurity amid escalating threats
- 8.2.4 CANADA
- 8.2.4.1 Concerning security lag in energy companies to drive need for CIP solutions and services
- 8.3 ASIA PACIFIC
- 8.3.1 ASIA PACIFIC: MARKET DRIVERS
- 8.3.2 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 8.3.3 CHINA
- 8.3.3.1 Surge in economic growth and technological innovation to drive market
- 8.3.4 JAPAN
- 8.3.4.1 Robust base of technologically advanced industries to drive market
- 8.3.5 INDIA
- 8.3.5.1 Digitalization transformation to spur demand for critical infrastructure
- 8.3.6 REST OF ASIA PACIFIC
- 8.4 EUROPE
- 8.4.1 EUROPE: MARKET DRIVERS
- 8.4.2 EUROPE: MACROECONOMIC OUTLOOK
- 8.4.3 UK
- 8.4.3.1 Increase in cyberattacks to drive need for critical infrastructure protection
- 8.4.4 GERMANY
- 8.4.4.1 Government initiatives to contribute to technological advancements by protecting critical infrastructures
- 8.4.5 FRANCE
- 8.4.5.1 ANSSI's initiatives for securing critical infrastructure to drive market
- 8.4.6 ITALY
- 8.4.6.1 Surge in cyberattacks exacerbated by rise in remote work to drive market
- 8.4.7 REST OF EUROPE
- 8.5 MIDDLE EAST & AFRICA
- 8.5.1 MIDDLE EAST & AFRICA: MARKET DRIVERS
- 8.5.2 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 8.5.3 GULF COOPERATION COUNCIL (GCC)
- 8.5.3.1 KSA
- 8.5.3.1.1 Flourishing economy driven by manufacturing and industrial sectors to drive market
- 8.5.3.2 UAE
- 8.5.3.2.1 Initiatives by CICPA and TRA to maintain security of critical infrastructure
- 8.5.3.3 Rest of GCC countries
- 8.5.3.1 KSA
- 8.5.4 SOUTH AFRICA
- 8.5.4.1 Comprehensive approach to infrastructure protection to drive market
- 8.5.5 REST OF MIDDLE EAST & AFRICA
- 8.6 LATIN AMERICA
- 8.6.1 LATIN AMERICA: MARKET DRIVERS
- 8.6.2 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 8.6.3 BRAZIL
- 8.6.3.1 Rise in adoption of advanced CIP technologies to drive market
- 8.6.4 MEXICO
- 8.6.4.1 Digital evolution to help enhance critical infrastructure protection
- 8.6.5 REST OF LATIN AMERICA
9 COMPETITIVE LANDSCAPE
- 9.1 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2022-2024
- 9.2 REVENUE ANALYSIS, 2020-2024
- 9.3 MARKET SHARE ANALYSIS, 2024
- 9.4 BRAND/PRODUCT COMPARISON
- 9.4.1 HONEYWELL
- 9.4.2 BAE SYSTEMS
- 9.4.3 THALES
- 9.4.4 NORTHROP GRUMMAN
- 9.4.5 MOTOROLA SOLUTIONS
- 9.5 COMPANY VALUATION AND FINANCIAL METRICS
- 9.5.1 COMPANY VALUATION
- 9.5.2 FINANCIAL METRICS
- 9.6 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 9.6.1 STARS
- 9.6.2 EMERGING LEADERS
- 9.6.3 PERVASIVE PLAYERS
- 9.6.4 PARTICIPANTS
- 9.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 9.6.5.1 Company footprint
- 9.6.5.2 Region footprint
- 9.6.5.3 Offering footprint
- 9.6.5.4 Vertical footprint
- 9.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 9.7.1 PROGRESSIVE COMPANIES
- 9.7.2 RESPONSIVE COMPANIES
- 9.7.3 DYNAMIC COMPANIES
- 9.7.4 STARTING BLOCKS
- 9.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 9.7.5.1 Detailed list of key startups/SMEs
- 9.7.5.2 Competitive benchmarking of key startups/SMEs
- 9.8 COMPETITIVE SCENARIO
- 9.8.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 9.8.2 DEALS
10 COMPANY PROFILES
- 10.1 INTRODUCTION
- 10.2 KEY PLAYERS
- 10.2.1 AXIS COMMUNICATIONS
- 10.2.1.1 Business overview
- 10.2.1.2 Products/Solutions/Services offered
- 10.2.1.3 Recent developments
- 10.2.1.3.1 Product launches/developments
- 10.2.1.3.2 Deals
- 10.2.2 FORCEPOINT
- 10.2.2.1 Business overview
- 10.2.2.2 Products/Solutions/Services offered
- 10.2.2.3 Recent developments
- 10.2.2.3.1 Product launches/developments
- 10.2.2.3.2 Deals
- 10.2.2.3.3 Other developments
- 10.2.3 FORTINET
- 10.2.3.1 Business overview
- 10.2.3.2 Products/Solutions/Services offered
- 10.2.3.3 Recent developments
- 10.2.3.3.1 Product launches/developments
- 10.2.3.3.2 Deals
- 10.2.4 CISCO
- 10.2.4.1 Business overview
- 10.2.4.2 Products/Solutions/Services offered
- 10.2.4.3 Recent developments
- 10.2.4.3.1 Product launches/developments
- 10.2.4.3.2 Deals
- 10.2.5 BAE SYSTEMS
- 10.2.5.1 Business overview
- 10.2.5.2 Products/Solutions/Services offered
- 10.2.5.3 Recent developments
- 10.2.5.3.1 Deals
- 10.2.5.4 MnM view
- 10.2.5.4.1 Key strengths
- 10.2.5.4.2 Strategic choices
- 10.2.5.4.3 Weaknesses and competitive threats
- 10.2.6 LOCKHEED MARTIN
- 10.2.6.1 Business overview
- 10.2.6.2 Products/Solutions/Services offered
- 10.2.6.3 Recent developments
- 10.2.6.3.1 Deals
- 10.2.6.4 MnM view
- 10.2.6.4.1 Key strengths
- 10.2.6.4.2 Strategic choices
- 10.2.6.4.3 Weaknesses and competitive threats
- 10.2.7 GENERAL DYNAMICS
- 10.2.7.1 Business overview
- 10.2.7.2 Products/Solutions/Services offered
- 10.2.7.3 Recent developments
- 10.2.7.3.1 Expansions
- 10.2.8 NORTHROP GRUMMAN
- 10.2.8.1 Business overview
- 10.2.8.2 Products/Solutions/Services offered
- 10.2.8.3 Recent developments
- 10.2.8.3.1 Product launches/developments
- 10.2.8.3.2 Deals
- 10.2.8.4 MnM view
- 10.2.8.4.1 Key strengths
- 10.2.8.4.2 Strategic choices
- 10.2.8.4.3 Weaknesses and competitive threats
- 10.2.9 HONEYWELL
- 10.2.9.1 Business overview
- 10.2.9.2 Products/Solutions/Services offered
- 10.2.9.3 Recent developments
- 10.2.9.3.1 Product launches/developments
- 10.2.9.3.2 Deals
- 10.2.9.4 MnM view
- 10.2.9.4.1 Key strengths
- 10.2.9.4.2 Strategic choices
- 10.2.9.4.3 Weaknesses and competitive threats
- 10.2.10 AIRBUS
- 10.2.10.1 Business overview
- 10.2.10.2 Products/Solutions/Services offered
- 10.2.10.3 Recent developments
- 10.2.10.3.1 Deals
- 10.2.11 THALES
- 10.2.11.1 Business overview
- 10.2.11.2 Products/Solutions/Services offered
- 10.2.11.3 Recent developments
- 10.2.11.3.1 Product launches/developments
- 10.2.11.3.2 Deals
- 10.2.11.4 MnM view
- 10.2.11.4.1 Key strengths
- 10.2.11.4.2 Strategic choices
- 10.2.11.4.3 Weaknesses and competitive threats
- 10.2.12 HEXAGON AB
- 10.2.12.1 Business overview
- 10.2.12.2 Products/Solutions/Services offered
- 10.2.12.3 Recent developments
- 10.2.12.3.1 Product launches/developments
- 10.2.12.3.2 Deals
- 10.2.13 JOHNSON CONTROLS
- 10.2.13.1 Business overview
- 10.2.13.2 Products/Solutions/Services offered
- 10.2.13.3 Recent developments
- 10.2.13.3.1 Product launches/developments
- 10.2.13.3.2 Deals
- 10.2.14 MOTOROLA SOLUTIONS
- 10.2.14.1 Business overview
- 10.2.14.2 Products/Solutions/Services offered
- 10.2.14.3 Recent developments
- 10.2.14.3.1 Product launches/developments
- 10.2.14.3.2 Deals
- 10.2.14.4 MnM view
- 10.2.14.4.1 Key strengths
- 10.2.14.4.2 Strategic choices
- 10.2.14.4.3 Weaknesses and competitive threats
- 10.2.15 TENABLE
- 10.2.16 ROLTA
- 10.2.17 SERVICENOW
- 10.2.18 LUNA-OPTASENSE
- 10.2.19 TELTRONIC
- 10.2.20 WATERFALL SECURITY SOLUTIONS
- 10.2.21 WESTMINISTER GROUP PLC
- 10.2.22 OWL CYBER DEFENSE SOLUTIONS
- 10.2.23 ACHILLES HEEL TECHNOLOGIES
- 10.2.24 CIPS SECURITY
- 10.2.25 SUPREMA INC
- 10.2.26 INDUSTRIAL DEFENDER
- 10.2.27 TERMA
- 10.2.28 ERICSSON
- 10.2.29 RHEBO AG
- 10.2.30 LEIDOS
- 10.2.31 MECOM MEDIEN-COMMUNICATIONS
- 10.2.32 KLOCH
- 10.2.33 SIEMENS
- 10.2.34 CAMBIUM NETWORKS
- 10.2.35 HUAWEI
- 10.2.36 G4S
- 10.2.37 GE VERNOVA
- 10.2.38 NEC CORPORATION
- 10.2.39 BRUKER CORPORATION
- 10.2.40 FUJITSU
- 10.2.1 AXIS COMMUNICATIONS
11 ADJACENT MARKETS
- 11.1 INTRODUCTION
- 11.1.1 LIMITATIONS
- 11.2 CYBERSECURITY MARKET
- 11.3 OPERATIONAL TECHNOLOGY (OT) SECURITY MARKET
12 APPENDIX
- 12.1 DISCUSSION GUIDE
- 12.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 12.3 AVAILABLE CUSTOMIZATIONS
- 12.4 RELATED REPORTS
- 12.5 AUTHOR DETAILS
















